关于COMThanasia
COMThanasia是一款针对COM对象的安全审计工具,可以帮助广大研究人员轻松检测COM对象中的各种安全问题。
功能介绍
1、检测COM对象(LaunchPermission、AccessPermission)中不正确的访问控制问题;
2、COM对象中不正确的注册表权限;
3、找到新的Elevation Moniker - UAC Bypass;
4、获取有关特定 CLSID 的详细信息;
5、检查低权限用户跨会话问题;
工具组成
当前版本的COMThanasia由一下几个组件组成:
PermissionHunter
ComDiver
MonikerHound
ClsidExplorer
ComTraveller
工具安装
广大研究人员可以直接使用下列命令将该项目源码克隆至本地:
git clone https://github.com/CICADA8-Research/COMThanasia.git
工具使用
PermissionHunter
PermissionHunter 是一个工具,它允许您检查系统上所有 COM 对象上的 LaunchPermission 和 ActivatePermission:
PS A:\mzhmo> .\PermissionHunter.exe -h
,
`-. \ .-'
,-"`````""-\__ | /
'-.._ _.-'` '-o,
_>--:{{< ) |)
.-'' '-.__.-o`
'-._____..-/` | \
,-' / `-.
`
PermissionHunter - hunt for incorrect LaunchPermission and ActivatePermission
CICADA8 Research Team
From Michael Zhmaylo (MzHmO)
PermissionHunter.exe
Small tool that allows you to find vulnerable COM objects with incorrect LaunchPermission and ActivatePermission
[OPTIONS]
-outfile : output filename
-outformat : output format. Accepted 'csv' and 'xlsx'
-h/--help : shows this windows
使用样例:
PS A:\mzhmo> .\PermissionHunter -outfile result -outformat xlsx
,
`-. \ .-'
,-"`````""-\__ | /
'-.._ _.-'` '-o,
_>--:{{< ) |)
.-'' '-.__.-o`
'-._____..-/` | \
,-' / `-.
`
PermissionHunter - hunt for incorrect LaunchPermission and ActivatePermission
CICADA8 Research Team
From Michael Zhmaylo (MzHmO)
[+] Result will be in result, format xlsx
[+] Success
输出内容如下:
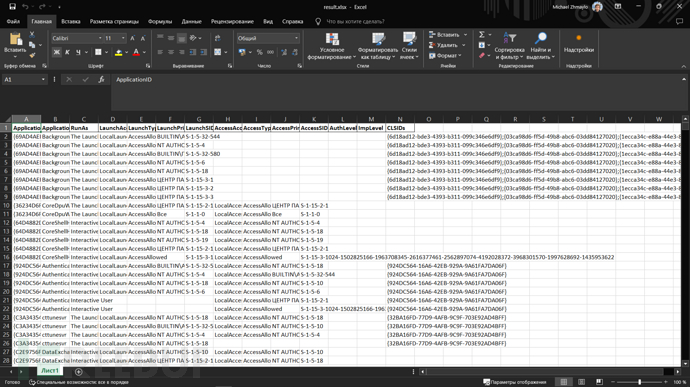
ComDiver
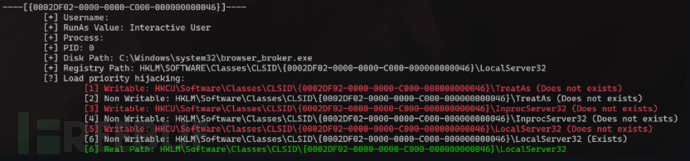
此工具可让您检测此类漏洞,并根据搜索 COM 对象时查看的键的优先级扫描注册表。通过这种方式,您甚至可以找到 Shadow COM Hijacking:
PS A:\ssd\gitrepo\COMThanasia\ComDiver\x64\Debug> .\ComDiver.exe -h \ / \ o ^ o / \ ( ) / ____________(%%%%%%%)____________ ( / / )%%%%%%%( \ \ ) (___/___/__/ \__\___\___) ( / /(%%%%%%%)\ \ ) (__/___/ (%%%%%%%) \___\__) /( )\ / (%%%%%) \ (%%%) ! ----------- COM DIVER -------------- [?] Small tool to check insecure registry and disk permissions on com objects [?] ARGS -h/--help <- show this message --from <CLSID> <- analyze CLSIDs from this clsid --target <CLSID> <- analyze one target clsid --no-context <- dont check another COM-server context. Only registry analyzing. --no-create <- dont create target COM object. This is the fastest mode
使用样例:
.\ComDiver.exe --no-create
MonikerHound
MonikerHound允许我们检测UAC绕过问题:
PS A:\ssd\gitrepo\COMThanasia\MonikerHound\x64\Debug> .\MonikerHound.exe
,_ _ _,
\o-o/
,(.-.),
_/ |) (| \_
/\=-=/\
,| \=/ |,
_/ \ | / \_
\_!_/
MonikerHound - find your own UAC Bypass!
CICADA8 Research Team
From Michael Zhmaylo (MzHmO)
[+] Potential COM server for elevation moniker found!
Name: CEIPLuaElevationHelper
CLSID: {01D0A625-782D-4777-8D4E-547E6457FAD5}
LocalizedString: @%systemroot%\system32\werconcpl.dll,-351
Enabled: 1
IconReference: @%systemroot%\system32\werconcpl.dll,-6
Activate: Success
PID: 15800
DllHost.exe
[+]........................[+]
[+] Potential COM server for elevation moniker found!
Name: CTapiLuaLib Class
CLSID: {03e15b2e-cca6-451c-8fb0-1e2ee37a27dd}
LocalizedString: @%systemroot%\system32\tapiui.dll,-1
Enabled: 1
IconReference: @%systemroot%\system32\tapiui.dll,-201
Activate: Success
PID: 440
DllHost.exe
[+]........................[+]
ClsidExplorer
ClsidExplorer 允许您检索有关特定 CLSID 的信息:
PS A:\ssd\gitrepo\COMThanasia\ClsidExplorer\x64\Debug> .\CLSIDExplorer.exe -h
CLSIDExplorer.exe - identify all info by clsid
Usage:
.\CLSIDExplorer.exe --clsid "{00000618-0000-0010-8000-00aa006d2ea4}"
使用样例:
PS A:\ssd\gitrepo\COMThanasia\ClsidExplorer\x64\Debug> .\CLSIDExplorer.exe --clsid "{00000618-0000-0010-8000-00aa006d2ea4}"
[{00000618-0000-0010-8000-00aa006d2ea4}]
AppID: Unknown
ProgID: Unknown
PID: 1572
Process Name: CLSIDExplorer.exe
Username: WINPC\\Michael
Methods:
[0] __stdcall void QueryInterface(IN GUID*, OUT void**)
[1] __stdcall unsigned long AddRef()
[2] __stdcall unsigned long Release()
[3] __stdcall void GetTypeInfoCount(OUT unsigned int*)
[4] __stdcall void GetTypeInfo(IN unsigned int, IN unsigned long, OUT void**)
[5] __stdcall void GetIDsOfNames(IN GUID*, IN char**, IN unsigned int, IN unsigned long, OUT long*)
[6] __stdcall void Invoke(IN long, IN GUID*, IN unsigned long, IN unsigned short, IN DISPPARAMS*, OUT VARIANT*, OUT EXCEPINFO*, OUT unsigned int*)
[7] __stdcall BSTR Name()
[8] __stdcall void Name(IN BSTR)
[9] __stdcall RightsEnum GetPermissions(IN VARIANT, IN ObjectTypeEnum, IN VARIANT)
[10] __stdcall void SetPermissions(IN VARIANT, IN ObjectTypeEnum, IN ActionEnum, IN RightsEnum, IN InheritTypeEnum, IN VARIANT)
[11] __stdcall void ChangePassword(IN BSTR, IN BSTR)
[12] __stdcall Groups* Groups()
[13] __stdcall Properties* Properties()
[14] __stdcall _Catalog* ParentCatalog()
[15] __stdcall void ParentCatalog(IN _Catalog*)
[16] __stdcall void ParentCatalog(IN _Catalog*)
[END]
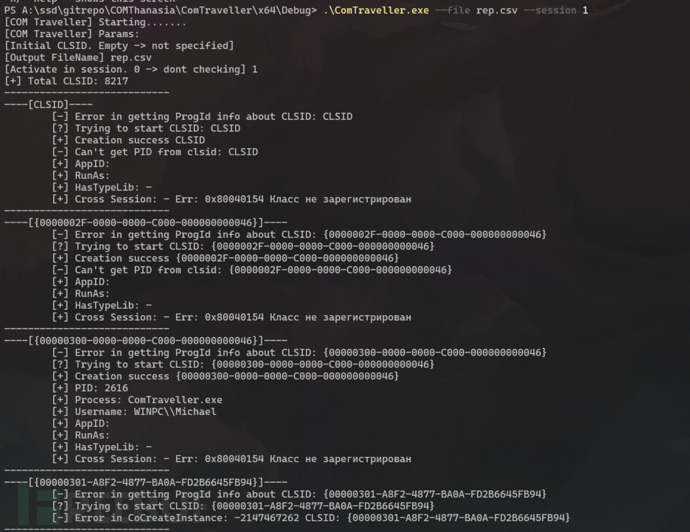
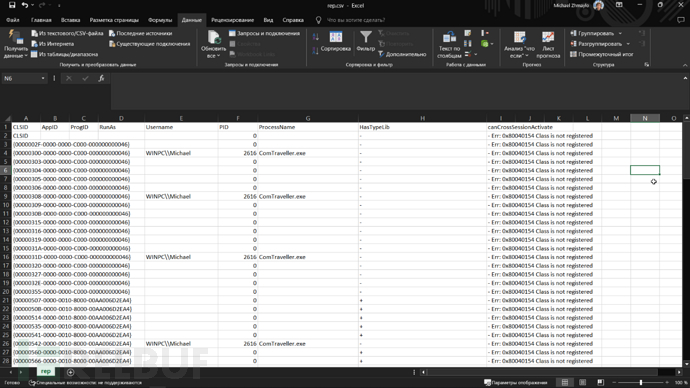
ComTraveller
此工具允许您探索所有可用的 COM 对:
PS A:\SSD\gitrepo\COMThanasia\ComTraveller\x64\Debug> .\ComTraveller.exe -h ,,_ zd$$??= z$$P? F:`c, _ d$$, `c'cc$$i ,cd$?R $$$$ cud$,?$$$i ,=P"2?z " $" " ?$$$,?$$$. ,-''`>, bzP 'cLdb,?$$,?$$$ ,h' "I$'J$P ... `?$$$,"$$,`$$h $$PxrF'd$" d$PP""?-,"?$$,?$h`$$,,$$'$F44" ?,,_`=4c,?=,"?hu?$`?L4$'? ' `""?==""=-"" `""-`'_,,,, .ccu?m?e?JC,-,"=? """=='?" ComTraveller - small tool to parse and extract information about all registered CLSIDs on the system Usage: --file <output> - output filename. Default: output.csv --from <clsid> - start exploring clsids from this clsid. (for ex. default enum from 1 to 9. with --from 4 will be from 4 to 9) --session <session> - use if you want to check Cross-Session Activation in a specific session. Useful only with 'Run as interactive user COM objects' --target <CLSID> - analyze this CLSID -h/--help - shows this screen
使用样例:
.\ComTraveller.exe --file rep.csv --session 1
项目地址
COMThanasia:【GitHub传送门】
参考资料
https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation/com-hijacking
4A评测 - 免责申明
本站提供的一切软件、教程和内容信息仅限用于学习和研究目的。
不得将上述内容用于商业或者非法用途,否则一切后果请用户自负。
本站信息来自网络,版权争议与本站无关。您必须在下载后的24个小时之内,从您的电脑或手机中彻底删除上述内容。
如果您喜欢该程序,请支持正版,购买注册,得到更好的正版服务。如有侵权请邮件与我们联系处理。敬请谅解!
程序来源网络,不确保不包含木马病毒等危险内容,请在确保安全的情况下或使用虚拟机使用。
侵权违规投诉邮箱:4ablog168#gmail.com(#换成@)


